What is the aim of an ARP spoofing attack?
ARP Spoofing attack is a part of MIMT also called the Man In the Middle Attack where the hacker intercepts the connection between the user and router and is able to see the data and also modify it.
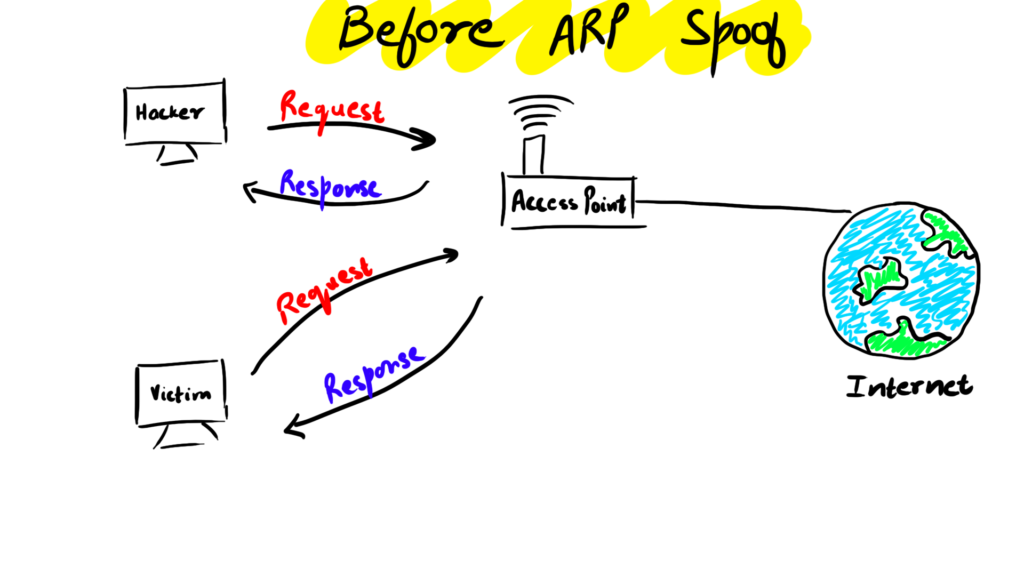
Before the ARP Spoofing attack, the Hacker's computer and the Victim's computer are only able to communicate with the router in form of requests and responses and the Hacker at that moment is not able to see what the victim is doing.
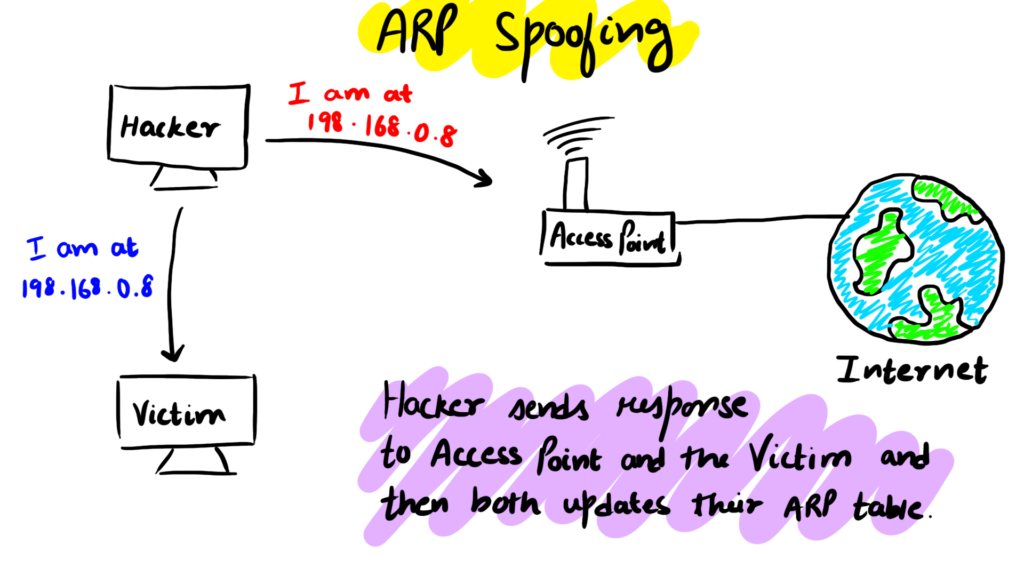
In the ARP Spoofing attack the Hacker does two things simultaneously
- Tells the Access point that it is at the Victim IP or it is actually the Victim.
- Tells the Victim that it is at the Access Point's IP or it is actually the Access Point
At this point, the Access Point believes that the Hacker is the Victim and the Victim believes that the Hacker is the Access Point.
After a successful ARP Spoofing attack now the data does not directly flow from Victim to the Access Point as before but it now travels through the Hacker's computer and now the Hacker can intercept the data in between and also read it.
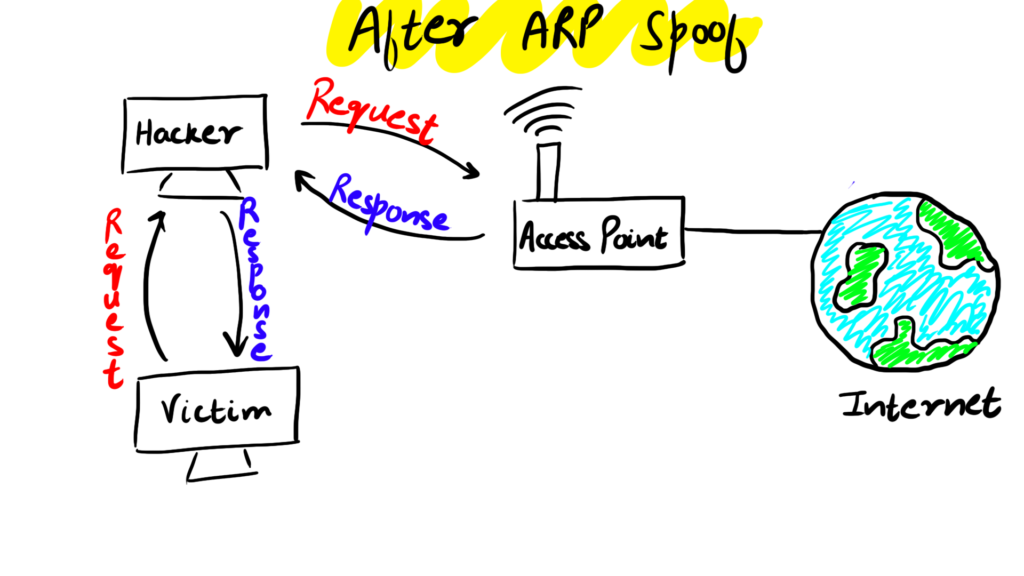
After a successful ARP Spoofing attack, both the Access Point and the Victim believes that things are normal and there is no problem.
What is ARP?
ARP is Address Resolution Protocol and it is a simple protocol used to map IP address of the machine to the MAC address of the machine
The computer that wants to communicate will send an ARP packet saying who has this IP and only the device with IP says that I have this IP and my MAC address is this.
Its point is to match or link the IP and MAC address of the device
There is a arp table which can be seen by doing
>> arp -a (both windows and linux)
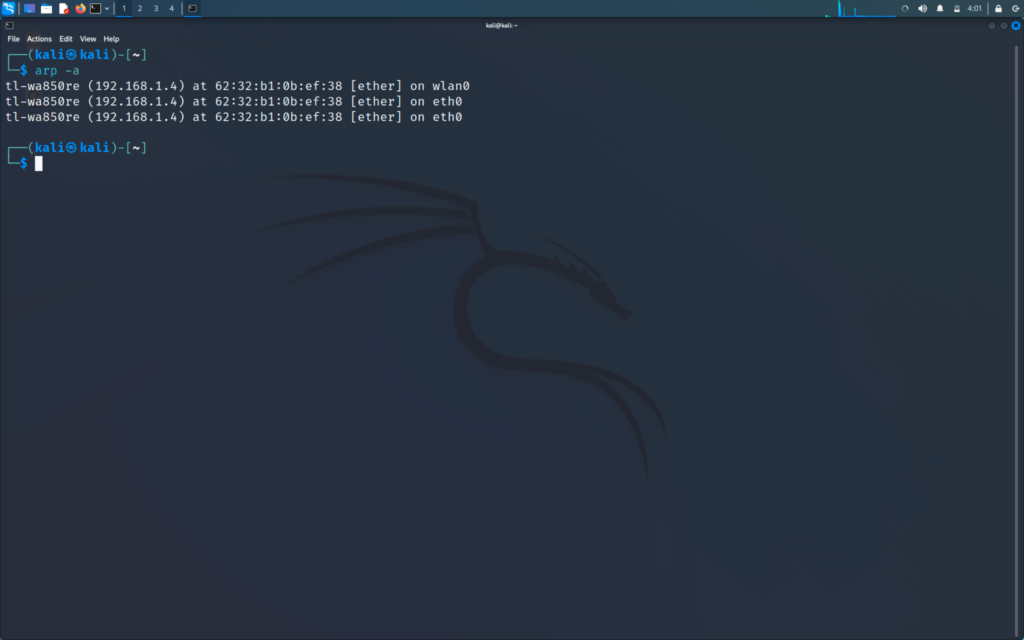
Now the MAC address can be modified by exploiting the ARP protocol.
Why the ARP Spoofing attack works?
The ARP Spoofing attack works mainly due to the following reasons :-
- ARP is not secure
- The clients accept the APR responses even if they haven't sent any request
- The clients also do not verify whether the ARP response is correct or not they just update their ARP table accordingly.
This weakness of the ARP protocol allows the ARP Spoofing attack possible
Also, do not let your curiosity fade away and increase your knowledge on ethical hacking and networking only on Hackers Paradise. Click below to learn more :
