OSI Transport Layer Functions
OSI Transport Layer
Before we go into the OSI Transport Layer Functions we should first have a general understanding of what is transport layer and then we can seen its functions.
This transport layer is the second layer in the TCP/IP model.
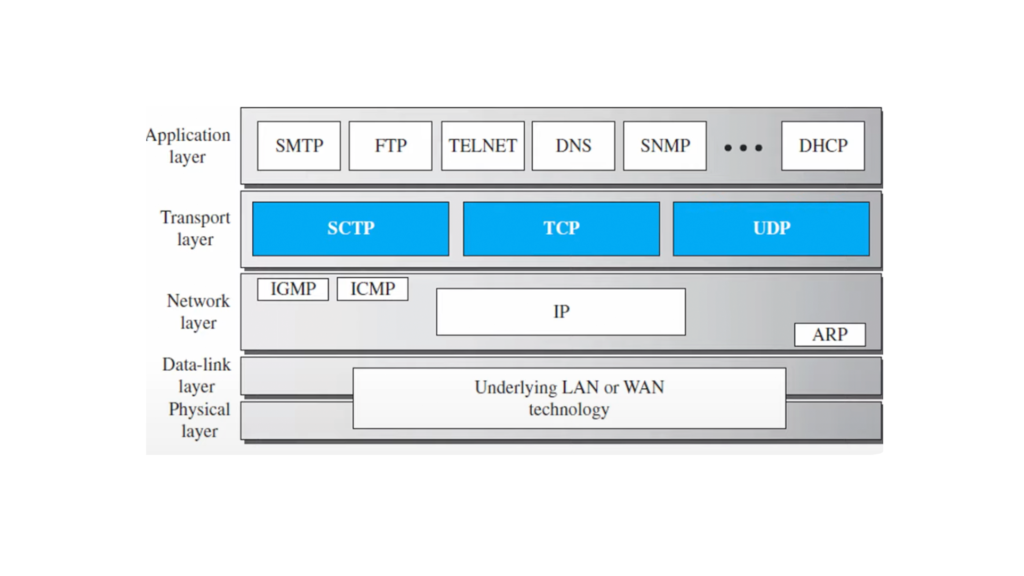
SCTP is a combination of the TCP and the UDP protocol
It works in the end-to-end delivery i.e when the information from one system reaches to the other system then the other system does not know in which application the information so this work is done by the application layer
For example, if we are using a chatting software like WhatsApp then when we send a message from WhatsApp to another person so that packet travels the network and in between, there may be different networks with different ISPs.
So once the message is received by the receiver’s operating system then that operating system does not know where to deliver this packet.
Here comes the role of the transport layer which selects the exact place to send the message and deliver the information correctly.
This is an end-to-end layer which is used to deliver messages to the host.
It is known as an end-to-end layer because it provides a point-to-point reliable connection rather than a hop-to-hop connection between the source host and destination host
In this layer, there is a segment which is the unit of data encapsulation in the transport layer
OSI Transport Layer Functions
Transport layer services
1.Process to Process communication
A process in the TCP/IP model is referred to as an entity which is running in the application layer that uses the services of the transport layer
2. Addressing - Port Numbers
There is a remote computer which can run several server programmes at the same time which is like your computer running many application at once.
Now you might be thinking why is there a need to have a specific set of new addresses when we already have the IP addresses ?
So when a packet is delivered form the sender IP to the host IP then the work of IP address is finished but then how will the IP know in which application to send this packet ?
This work is done by the Port Numbers which are unique for every type of application and then by using Port Numbers it becomes easy for the sender to send the data packets to the receiver and properly utilise it.
Eg Web Browsers have port 80
Now to use the services of the transport layer in the internet we will need a pair of socket addresses
The pair of socket addresses are:-
Client socket address
Server socket address
Encapsulation and Decapsulation
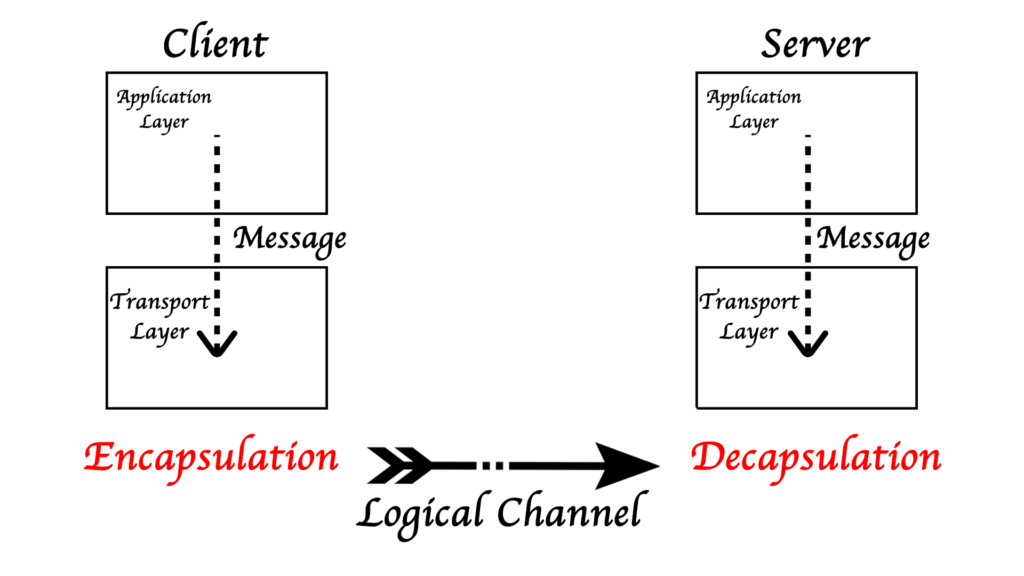
When data is send in a network it is a long form of 0s and 1s and the computer does not know when to stop it but as humans we know it so we have made this transport layer in which sets of data are encapsulated which are then called as segments and then sent to the receiving end where the packets are then decapsulated i.e the segment is opened.
Multiplexing and Demultiplexing
Multiplexing is whenever an entity or commonly a device is receiving items from more than one source i.e many to one
This taking of the packets is done in a sequential order which means that all the packets are not dumped at once.
Demultiplexing is whenever an entity or commonly a device is sending items to more than one source i.e one to many
Flow control
In a network, an entity consumes the packets and another entity produces them so there should be a balance between production and consumption rates.
There are mainly two ways of pulling and pushing which are :-
Pushing and Pulling
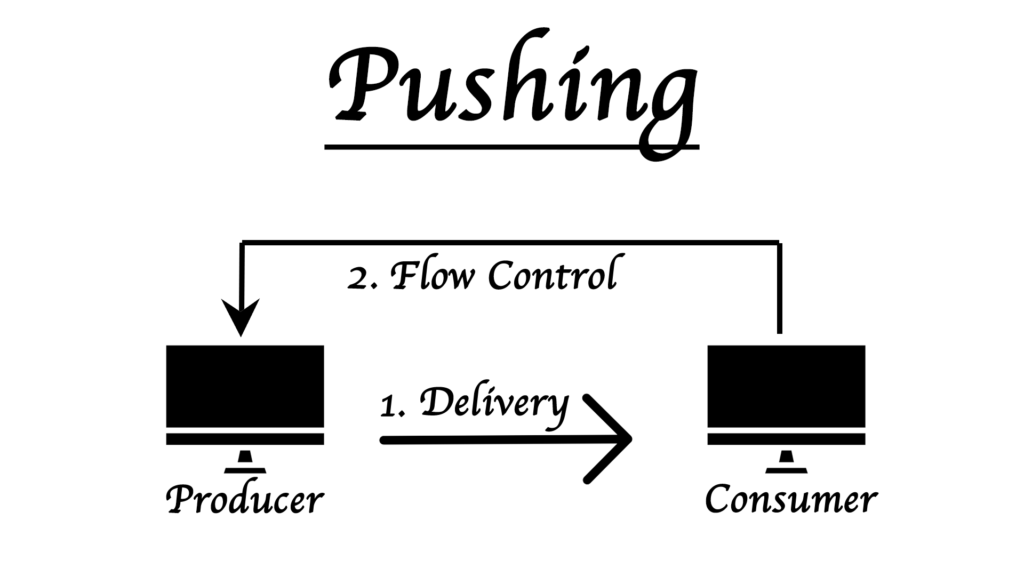
In pushing first the producer continuously sends the packets to the consumer and then the consumer tells the producer to stop or how much data to send in one go.
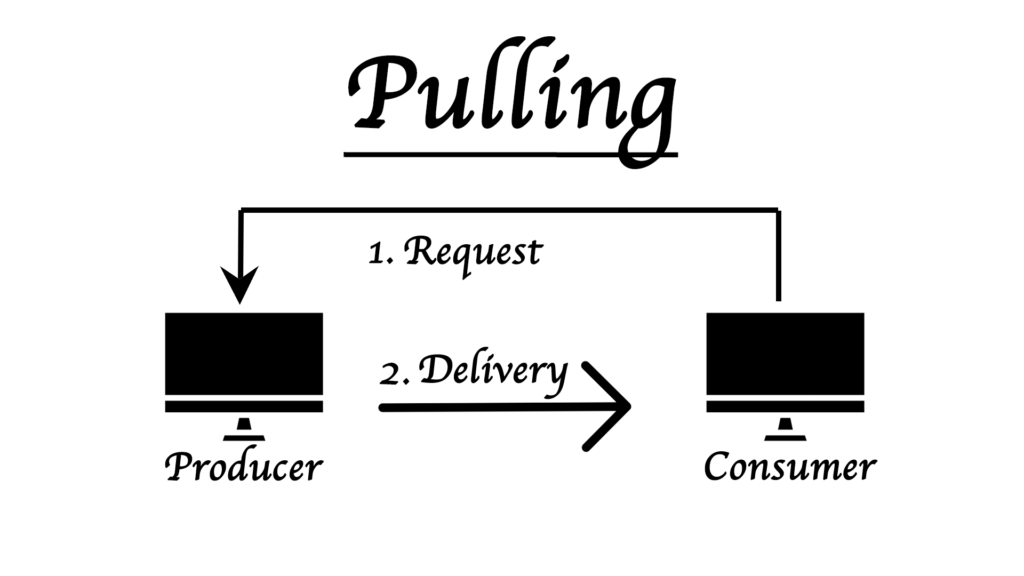
In pulling first the consumer requests the producer to send the packets and also specifies the size and rate and the only the producer sends the message.
Buffers
These are a set of the memory location in the location between the sender and the receiver in the network
Error Control
Since the layer is underlying the transport layer i.e the network layer which has IP in it is unreliable we need to make the transport layer more reliable
The error control methods in the transport layer are responsible for:-
- Detecting the corrupted packets
- Discarding the corrupted packets
- Buffering the out-of-order packets till the missing packets arrive
- Keeping track of the packets that are lost and discarded and then resending them
- Recognising the duplicate packets and then discarding them
Sequence Numbers
Then packets when sent in the network from the sender to the receiver then they are numbered sequentially.
Now as we need to include these number of packets in the header of each packet hence we need to set a limit
So if the header in the packet has allotted n bits for the sequence number then the sequence number range from 0 to 2n-1
Acknowledgement
The receiver sides whenever receives a collection of packets can send an acknowledgement packet (ACK) stating that the packets have arrived safe and sound
Whenever a packet is sent from the sender's side the sender starts a timer and if the acknowledgement packet (ACK) does not arrive before the time expires the sender then resends the packet
There are two types of acknowledgement
Positive Acknowledgement
This packet is sent by the receiver to the sender to let the sender know that the packet is received
Negative Acknowledgment
If after a certain time the packet is not received by the receiver then it sends this to tell that the packet is not received
Congestion Control
Congestion in the network can occur if the load on the network is more than the network capacity i.e the packets sent to the network is greater than the network’s capacity
