In this post, I will be discussing how to detect hackers on your network and keep yourself safe in the malicious internet world.
Nowadays it is very easy to to get malicious softwares and viruses on our computer as whenever we download something from internet it always possesses a risk of having malicious programme.
Also many people nowadays install pirated software and pirated movies which are the most potent source of malicious software nowadays in internet.
DETECTING THE ARP SPOOFING ATTACK
How to detect Hackers on your network?
First of all you should know that detecting a hacker on your network is not a easy task as the hacker on the other end is trying its best to not get caught. Also the hacker is trained to hide in a system but in general we are not trained to find such hacker on our system so this becomes a bit of a challenging task.
What is ARP spoofing?
ARP Spoofing is a type of attack in which the hacker fools the router into believing that it is the client and fools the client into believing that is the router.
Thus hacker becomes the Man In the Middle and is able to intercept the data and analyse it.
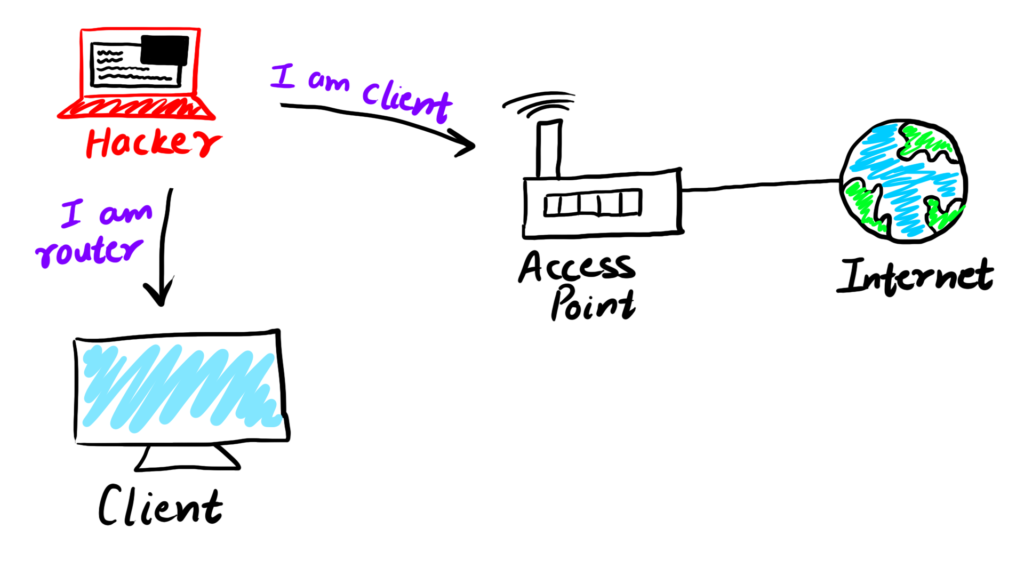
Why does ARP spoofing work?
ARP Spoofing attack works due to the following reasons :
- Clients accept the responses even if they have not sent any request
- Clients also trust the responses without any kind of verification
In this tutorial, the windows machine is the machine of the victim and the kali Linux machine is the hacker’s machine
Now every computer has an ARP table which can be seen by the command “arp -a”
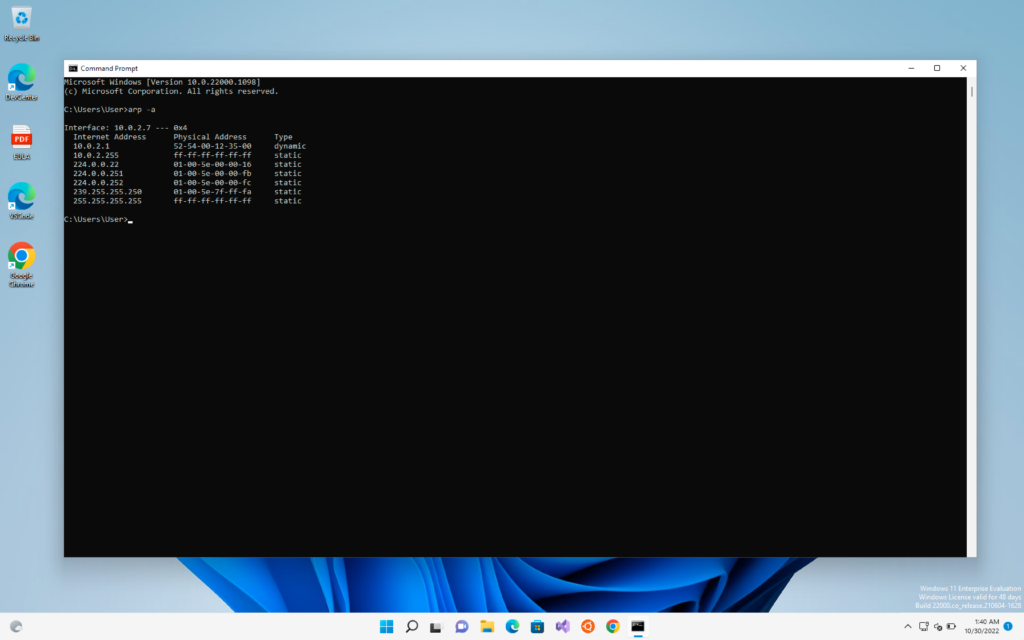
What is an ARP table?
So ARP table is just a table which contains the IP and MAC addresses of different computers.
It associates the IP addresses of the computers with the MAC address of the computers.
What happens during an ARP Poisoning Attack?
During an ARP poisoning attack, the ARP table of the victim is updated and its router MAC changes and becomes the MAC address of the hacker machine.
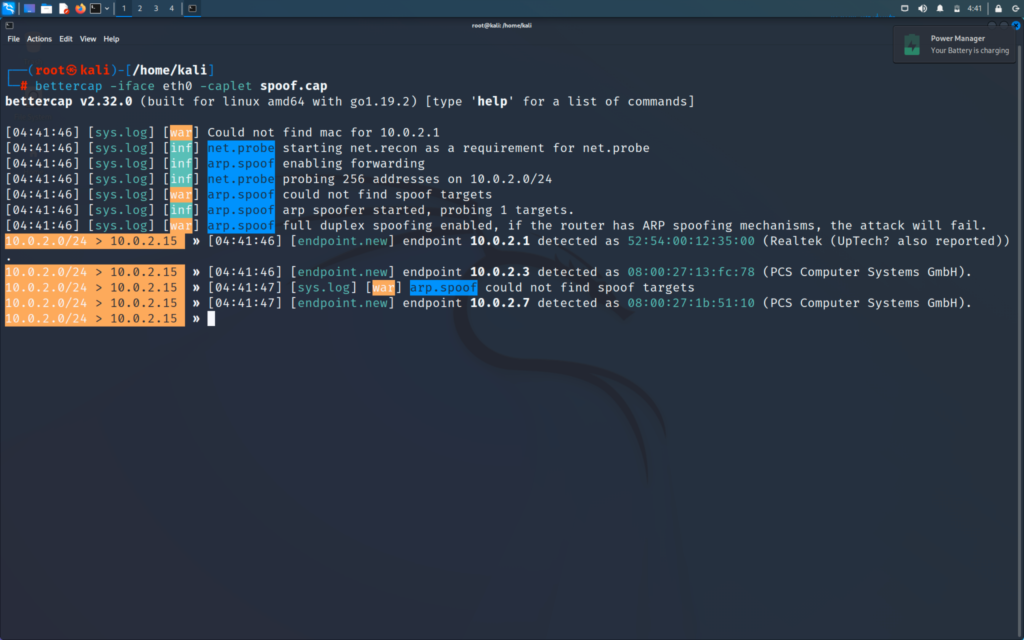
Now I will perform a ARP Spoof attack from the hacker machine and then we will see how the MAC gets changed in the victim’s machine
Running the ARP Spoof attack
The updated arp table in victims computer
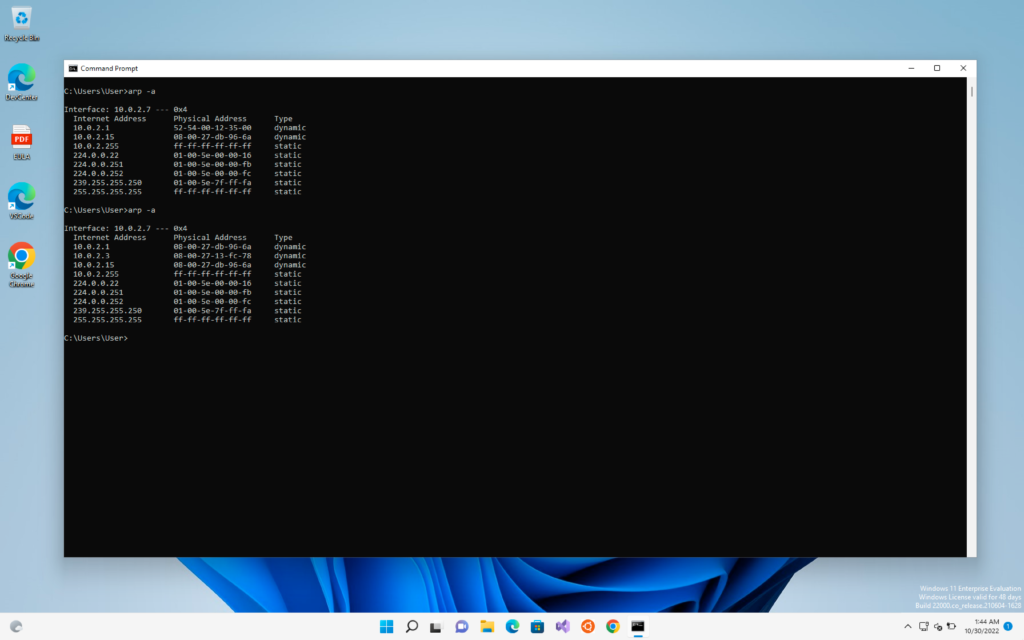
This is the easiest way to check the ARP poisoning attack but it is not at all practical as we have to constantly run the arp -a command and monitor it
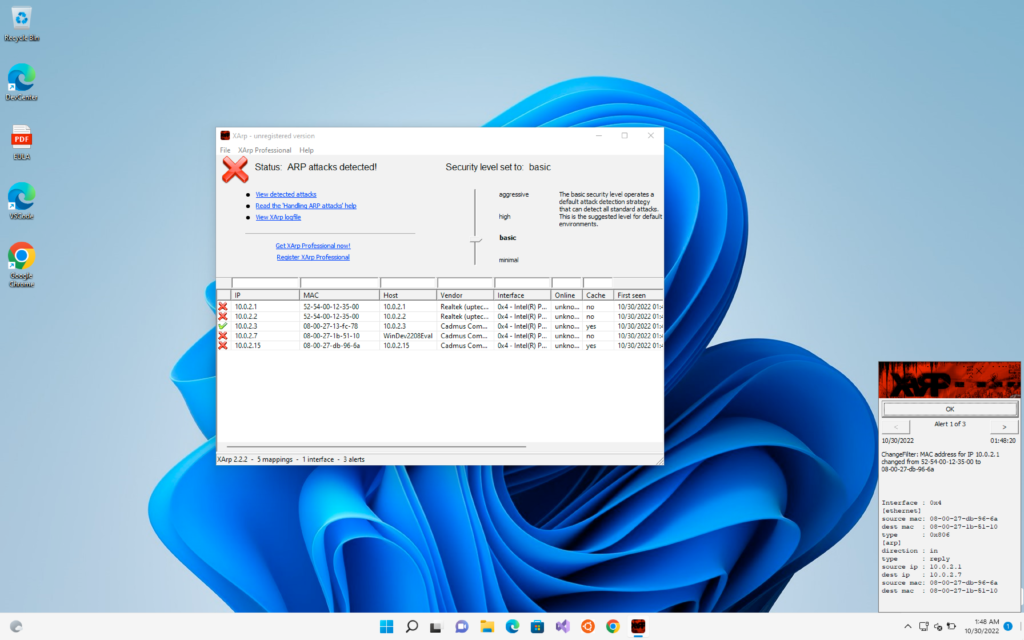
So for this there is a very good tool called XArp which is available for both linux and windows
We can download it from the link below
Now for the time being I have stopped the ARP Spoofing / Poisoning attack and we will run the tool
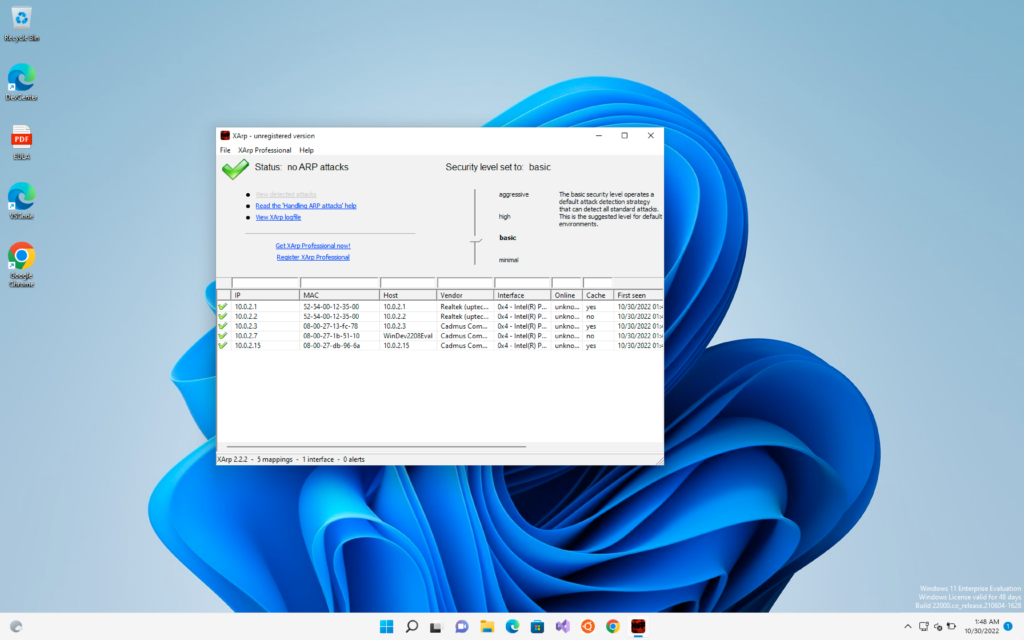
Now I will again start the ARP attack and we can see that XArp as detected the attack
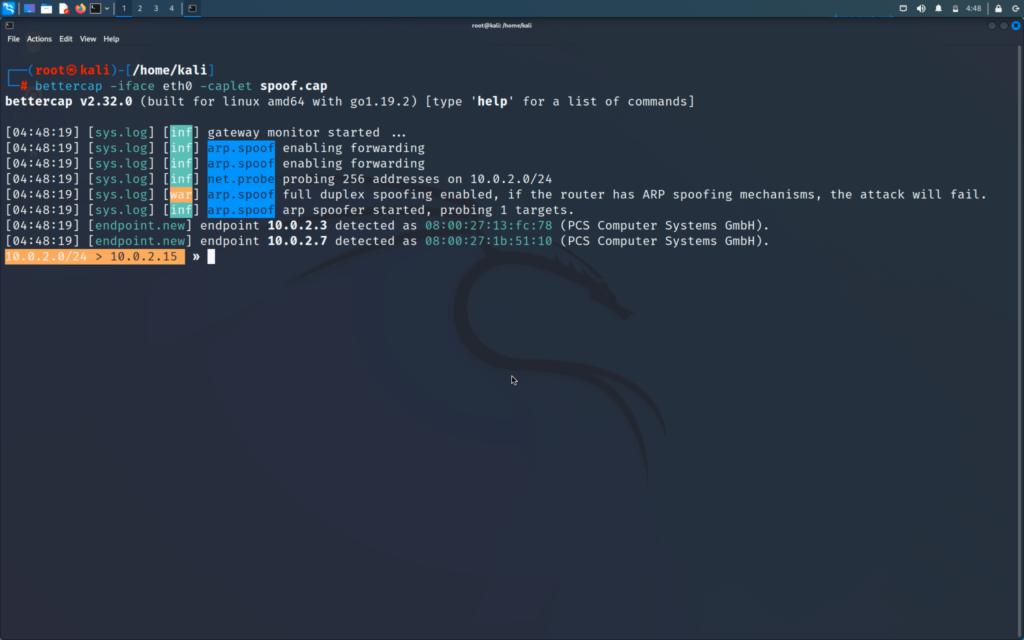
If you are interested on how you can also perform this ARP spoofing attack you can check my post below
=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0=0
USING WIRESHARK TO DETECT SUSPICIOUS ACTIVITIES
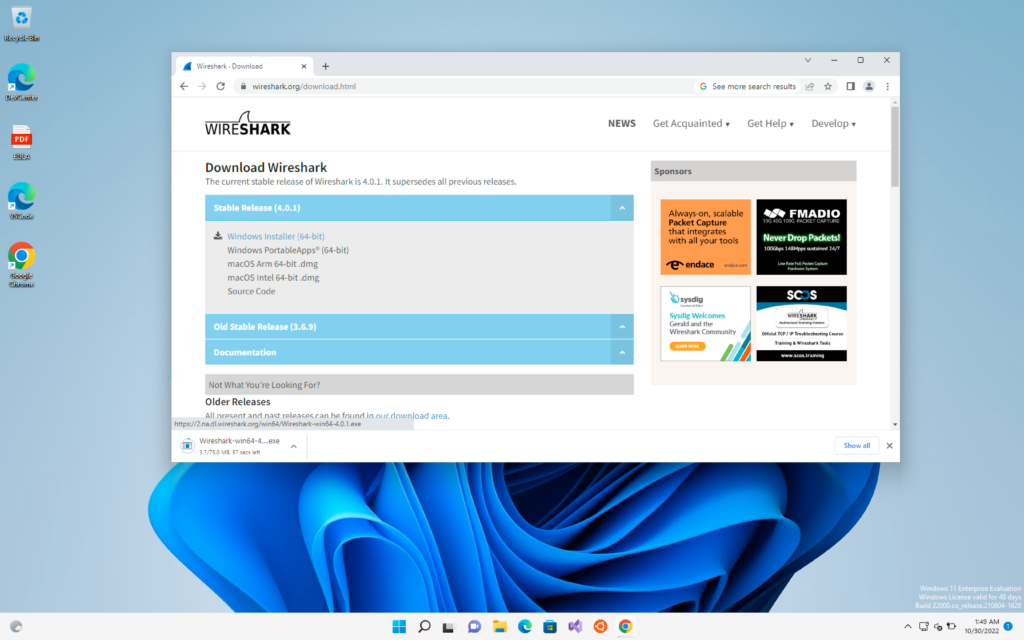
First, we will open Wireshark in our victim machine which can be easily downloaded from Google or you can use the link below to directly go to the Wireshark download page
https://www.wireshark.org/download.html
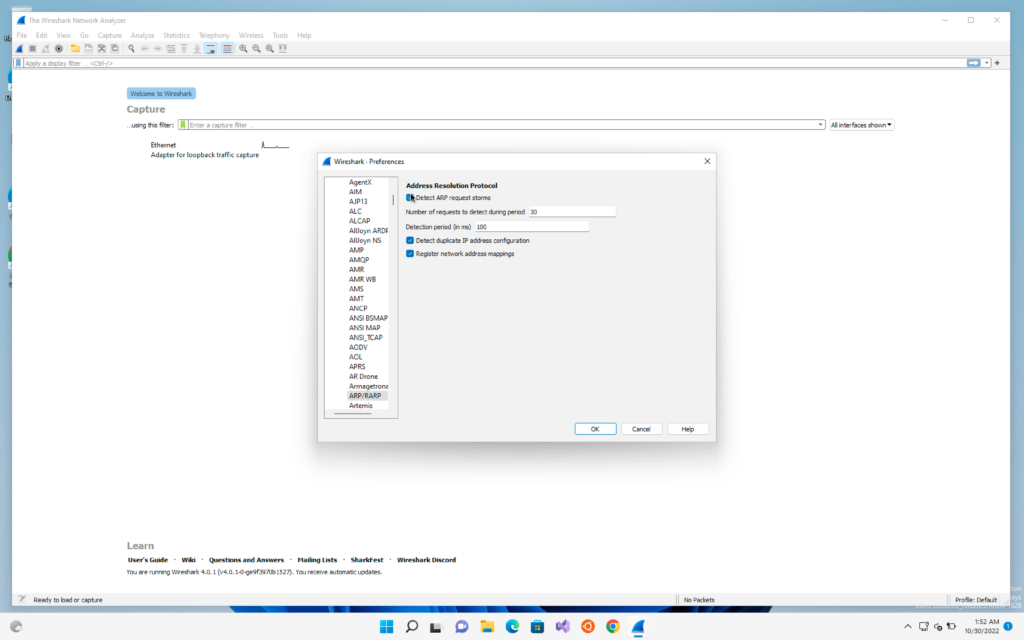
Now we will go to Edit -> Preferences -> protocols -> ARP
We will check on the Detect ARP request storms
And now we will start the capture
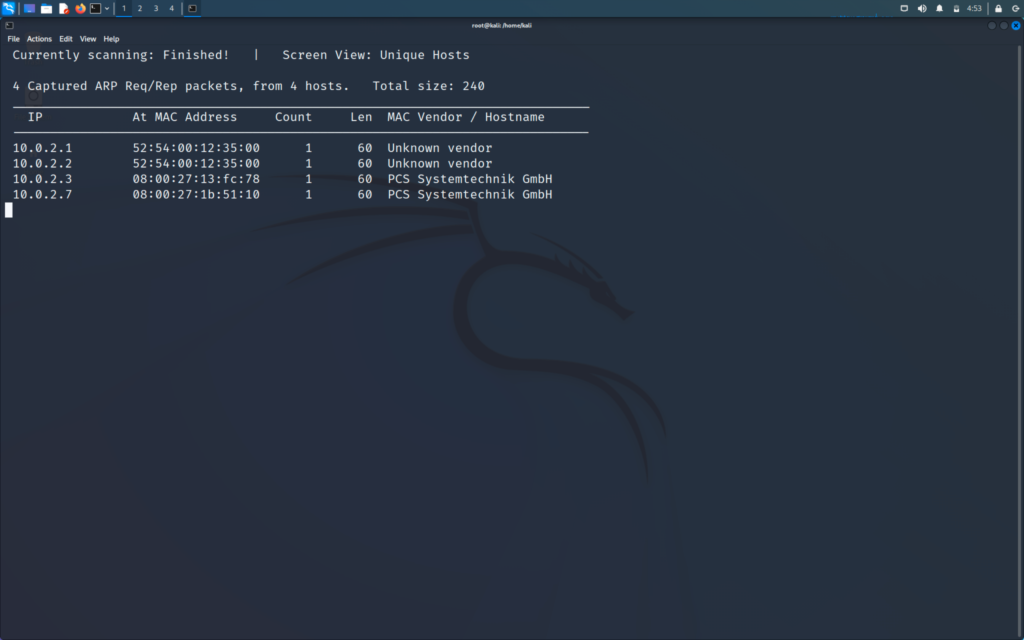
Now I will go to my hacker machine and start discovering client attack using netdiscover
>> netdiscover -i eth0 -r IP range/24
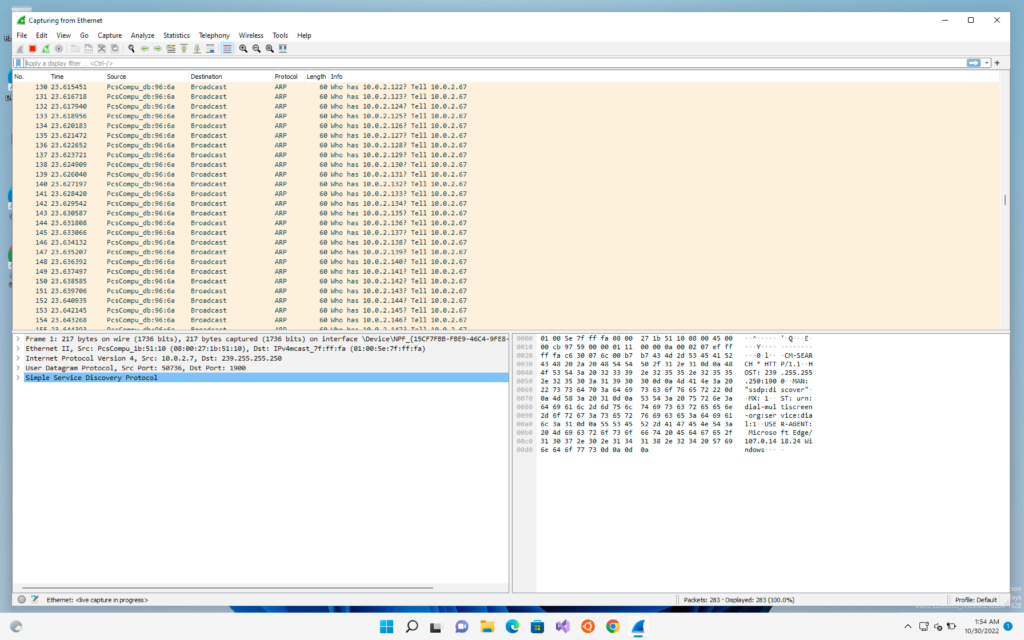
Now we will go to our victim windows machine and see the generated packets
We can see under the info column the last column that it is asking who has this IP and tell to this IP
Now we will click on Analyse -> Expert information
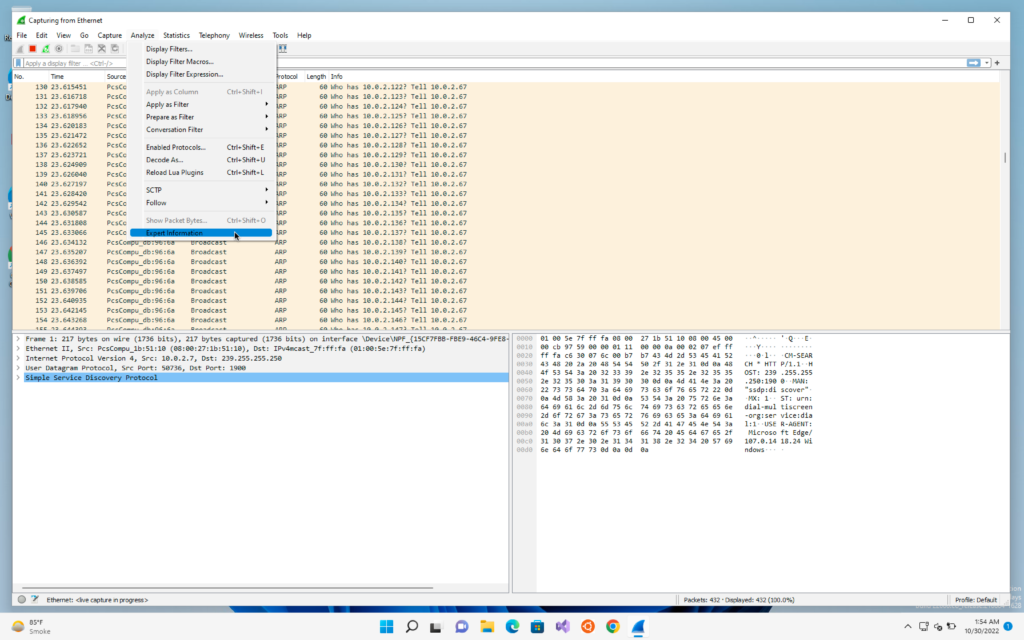
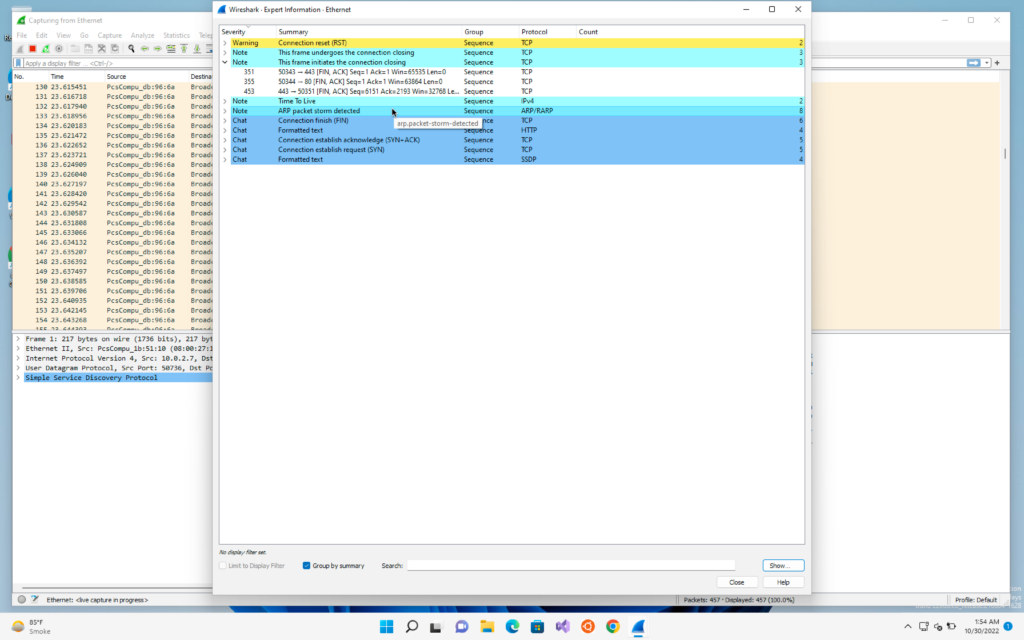
We will be able to see that it has detected a ARP storm. This means that there was a single device that have sent many packets. This gives us the signal that someone is trying to detect all the devices in its range and probably trying to perform a attack.
Now I will perform a ARP spoofing attack from my hacker machine
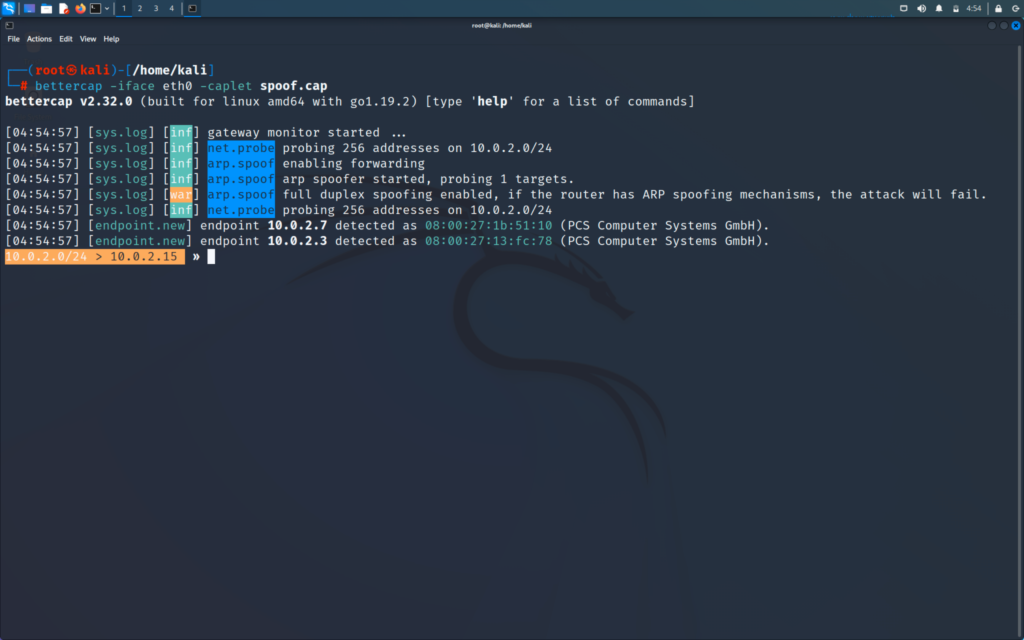
We will now check in Wireshark that what it has detected
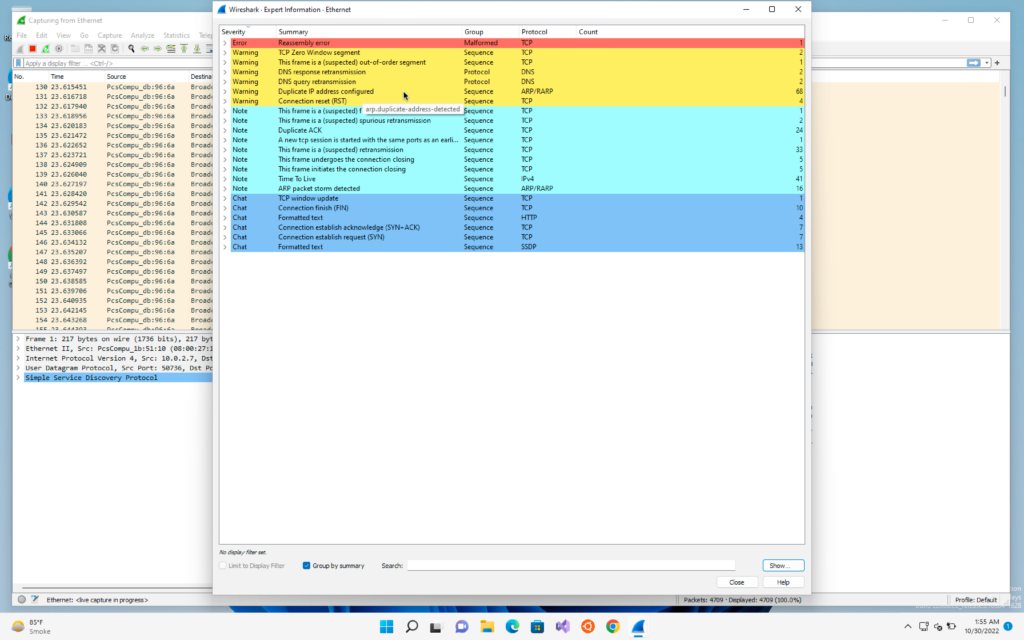
We will again go on Analyse -> Expert Information
We will see a warning that a duplicate IP address configured. This means that someone is trying to perform a ARP Poisoning attack and trying to place them in middle of the connection
PREVENTING ARP ATTACK
First we will go to the victim machine and keep in mind that the victim machine is we the normal user who are surfing the internet on a day-to-day basis
We will do the command “arp -a”
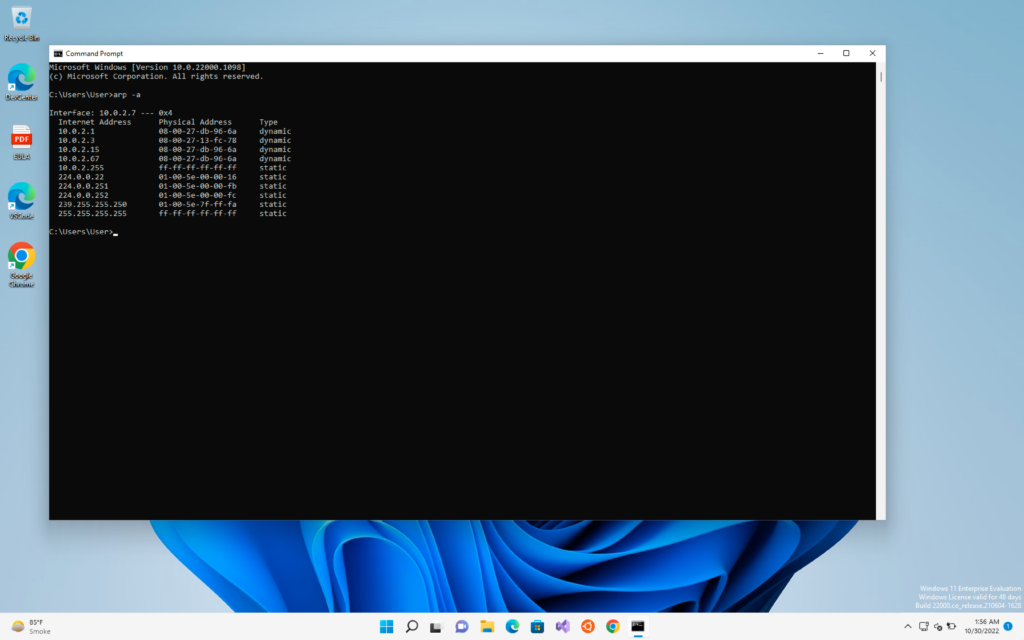
In the table we can see on the first internet address that under the type column it is written as dynamic which means the values can be changed
There we can also see are some static values which the system will never allow to change
We can use static ARP table in which we have to manually map the IP address to the MAC address and after that even if the Hacker uses the best tools it will not be able to perform the ARP spoofing attack
But this has a downside which is whenever you will connect to a new network or a device wants to join to your computer each time you have to manually configure the table
It is not practical to use if you are in a big company or a large network. But form small organisations and home network this can be useful.
Other useful ways to prevent these attacks it to always :
- Use HTTPS over HTTP
- Use a VPN if possible
I will be covering the above two ways also soon.
